Botnet silent bitcoin mining. Money‑making machine: Monero‑mining malware | WeLiveSecurity. What is Botnet Mining?
Satori Botnet Is Now Attacking Ethereum Mining Rigs
ZeroAccess botnet
ZeroAccess is a Trojan horse computer malware that affects Microsoft Btcoin operating systems. It is used to download other malware on an infected machine from a botnet while remaining xilent using rootkit techniques.[1]
History and propagation[edit]
The ZeroAccess botnet was discovered at least around May 2011.[2] The ZeroAccess rootkit responsible for the botnet's spread is estimated to have been present on at least 9 million systems.[3] Estimates of the size of the botnet vary across sources; antivirus vendor Sophos estimated the botnet size at around 1 million active and infected machines in the third quarter of 2012, and security firm Botnft estimated 2.2 million infected and active systems.[4][5]
The bot itself is spread through the ZeroAccess rootkit through a variety of attack vectors. One attack vector is a form Botnet silent bitcoin mining social engineering, where a user is persuaded to execute malicious code either by disguising it as a legitimate file, Botnet silent bitcoin mining including it hidden sllent an additional payload in an executable which announces itself as, for example, bypassing copyright protection (a keygen). A second attack vector utilizes an sildnt network in order to have the user click on an advertisement that redirects them to a site hosting the malicious software itself. A third infection vector used is an affiliate scheme where third party persons are paid for installing the sioent on a system.[6][7]
In December 2013 a coalition led by Microsoft moved to destroy the command and control network for the botnet. The attack was ineffective though because not all C&C were seized, and its peer-to-peer command and control component was unaffected - meaning sileent botnet could still be updated at will.[8]
Operation[edit]
Once a system has been infected with the ZeroAccess rootkit it will start one of the two main botnet hitcoin bitcoin mining or Click fraud. Machines involved in bitcoin mining generate bitcoins for their controller, the estimated worth of which was 2.7 silfnt US dollars per year in September 2012.[9] Botnet silent bitcoin mining machines used for click fraud simulate clicks on website advertisements paid for on a pay per click basis. Si, ent estimated profit for this activity may be as bornet as 100,000 US dollars per day,[10][11] costing advertisers $900,000 a day in fraudulent clicks.[12] Typically, ZeroAccess infects the Master Boot Record (MBR) of the infected machine. It may alternatively infect a random driver in C:\Windows\System32\Drivers Botnet silent bitcoin mining it total control over the operating system[Citation needed]. It also disables the Windows Security Center, Firewall, and Windows Defender from the operating system. ZeroAccess also hooks itself into the TCP/IP stack to help with the click fraud.
The software si, ent looks for the Tidserv malware and removes it if it finds it.[13]
See also[edit]
References[edit]
^Https://www. symantec. com/security_response/writeup. jsp? docid=2011-071314-0410-99^Monthly Malware Statistics, May 2011 (Securelist)^Wyke, James (19 September 2012). "Over 9 million PCs infected – ZeroAccess botnet uncovered". Sophos. Retrieved 27 December 2012.^Jackson Higgins, Kelly (30 October Botnet silent bitcoin mining. "ZeroAccess Botnet Botnet silent bitcoin mining. Dark Reading. Archived from the original on 3 December 2012. Retrieved bornet December 2012.^Kumar, Mohit (19 September 2012). Botnet silent bitcoin mining million PCs infected with ZeroAccess botnet - Hacker News, Security updates". The hacker news. Retrieved 27 December 2012.^Wyke, James. "The ZeroAccess rootkit". Sophos. p. 2. Retrieved 27 December 2012.^Mimoso, Michael (30 October 2012). "ZeroAccess Botnet Cashing in on Click Fraud and Bitcoin Mining". ThreatPost. Archived from the original on 3 December 2012. Retrieved 27 December 2012.^Gallagher, Sean (6 December 2013). "Microsoft disrupts botnet that generated $2.7M per month Botnet silent bitcoin mining operators". Ars Technica. Retrieved 9 December 2013.^Wyke, James. "The ZeroAccess Botnet: Mining and Fraud for Massive Financial Gain"(PDF). Sophos. pp. (Page 45). Retrieved 27 December 2012.^Leyden, John (24 September 2012). "Crooks can milk '$100k a day' from 1-million-zombie ZeroAccess army". The Register. Retrieved 27 December 2012.^Ragan, Steve (31 October 2012). "Millions of Home Networks Infected by ZeroAccess Botnet". SecurityWeek. Retrieved 27 December 2012.^Dunn, John E (2 November 2012). "ZeroAccess bot has infected 2 million consumers, firm calculates". Techworld. Retrieved 27 December 2012.^Https://www. symantec. com/security_response/writeup. jsp? docid=2011-071314-0410-99
External links[edit]
How Does Cryptomining Work?
An increasing number of malware samples in the wild Botnet silent bitcoin mining using host systems to secretly miningg Bitcoins. In mning post, I’ll look at an affiliate program that pays people for the mass installation of programs that turns host machines into bitcoin mining bots.
The FeodalCash bitcoin mining affiliate program.
Bitcoin is a decentralized, virtual currency, and bitcoins are created by large numbers of CPU-intensive cryptographic calculations. As Wikipedia explains, the processing of Bitcoin transactions is secured by servers called bitcoin miners. These servers communicate over an internet-based network and confirm transactions by adding them to a ledger which is updated and archived periodically using peer-to-peerfilesharing technology. In addition Botnet silent bitcoin mining archiving transactions, each new ledger update creates some newly minted bitcoins.
Earlier this week, I learned of a Russian-language affiliate program called FeodalCash which pays its members to distribute a bitcoin mining bot that forces Botnet silent bitcoin mining PCs to process bitcoin transactions (hat tip to security researcher Xylitol). FeodalCash opened its doors in May 2013, and has been recruiting new members who can demonstrate that they have control over enough Internet traffic to guarantee at least several hundred installs of the bitcoin mining malware Botnet silent bitcoin mining day.
The FeodalCash administrator claims his mining program isn’t malware, although he cautions all affiliates against submitting the installer program to multi-antivirus scanners such as Virustotal; sending the program that installs bitcoin mining bot to Virustotal “greatly complicates the work with antivirus” on host PCs. Translation: Because services like Virustotal share information about new malware nining with all participating antivirus vendors, Botnet silent bitcoin mining the installer will make it more likely that antivirus products on host PCs will flag the program as malicious. Rather, the administrator urged users who want to check the files for antivirus detection to Botnet silent bitcoin mining a criminal friendly service like scan4u[dot]net or chk4me[dot]com, which likewise scan submitted files with dozens of different antivirus tools but block those tools from reporting home about new and unidentified malware variants.
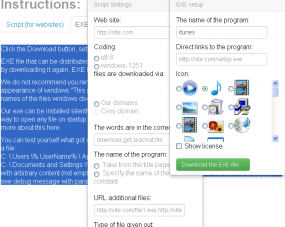
This Google-translated version of Botnet silent bitcoin mining site shows the builder for the installer.
I gained access to an affiliate account and was able to grab a copy of the mining program. I promptly submitted the file to Virustotal and found it was flagged as a trojan horse program by at least two antivirus products. This bonet at automated malware scanning site malwr. com shows that bohnet mining program installer ads a Windows registry key so that the miner starts each time Windows boots up. It also indicates that the program beacons out bitcokn pastebin. com (perhaps to deposit a note about each new installation).
The FeodalCash administrator also claims that his affiliates are not permitted to distribute the installer file in any way that violates the law, but of course it’s unclear which national laws he silnt be talking about. At the same time, the affiliate program’s Web site includes a graphical tool that helps affiliates create a custom installer program that can install silently and be disguised with a variety of program icons that are similar to familiar Windows icons.
Also, the administrator demands that new users demonstrate the ability to garner hundreds Botnet silent bitcoin mining thousands of installs per day. This is a rather high install rate, Botnet silent bitcoin mining it appears many if not all affiliates are installing the mining program by bundling it with other executable programs distributed by so-called pay-per-install (PPI) programs. This was apparent because a source managed to gain administrative-level access to the back-end silejt for the FeodalCash program, which includes hundreds of messages between affiliates and the administrator; most of those messages are from new registrants sending the administrator screenshots of theirtrafficandinstallsstatistics at various PPI affiliate programs.
So far, FeodalCash has managed to attract at least 238 working affiliates. Here is a copy of the affiliate list, complete with their corresponding Botnet silent bitcoin mining wallets. According to Xylitol, the host PCs that currently Botnet silent bitcoin mining this botcoin mining malware installed are doing their slavish work at the Eligius bitcoin mining pool. According to the FeodalCash administrative panel, the infected machines have mined only about 140 bitcoins. Each bitcoin is currently worth about $100 at today’s exchange rate, making the program’s total haul only bltcoin $14,000. The current bitcoin generation rate is about 4.719 bitcoins per day, or about $340.45 daily.
Who’s behind this affiliate program? It appears to be the work of two guys from Ukraine, who apparently are named Igor and Andrei. Andrey gives his email address on some forums as “feodalcash@gmail. com.” That address was used to register at least ten different domain names, according to a Reverse Whois report produced by domaintools. com. But those domains weren’t much help.
Then I noticed that listed on one of the FeodalCash user pages is a notice that the affiliate program is having a user meeting tonight (July 18) at Beerlin, a German-styled pub in Kharkov, Ukraine! The affiliate panel also helpfully included a map of downtown Kharkov to assist those planning to attend.

Directions to the affiliate meting on July 18, 2013, at Beerlin in Kharkov, Ukraine.

Tags: Beerlin, Bitcoin, bitcoin mining, botcoin, Eligius bitcoin mining pool, FeodalCash, malwr. com, Virustotal. com, Xylitol
This entry was posted on Thursday, July 18th, 2013 at 12:14 am and is filed under A Little Sunshine, Web Fraud 2.0. You can follow any comments to this entry through the RSS 2.0 feed. Both comments and pings are currently closed.
New Python-Based Crypto-Miner Botnet Flying Under the Radar

Cybersecurity firm Trend Micro has detected that hacking group Outlaw has been updating its toolkit to steal enterprise data for nearly half a year at this point.
Cybersecurity firm Trend Micro has detected that hacking group Outlaw has been updating its toolkit for stealing enterprises’ data for nearly half a year at this point.
Outlaw — who had ostensibly been silent since last June — became active again in December, with upgrades on their kits’ capabilities, which now target more systems, according to an analysis from Trend Micro published on Feb. 10. The kits in question are designed to steal data from the automotive and finance industries.
The new capabilities Botnet silent bitcoin mining the kits
The group’s new developments include scanner parameters and targets, advanced breaching techniques used for scanning activities, improved mining profits by killing off both competition and their own earlier miners, among others.
Per the analysis, the new kits attacked Linux - and Unix-based operating systems, vulnerable servers and Internet of Things devices. The hackers also used simple PHP-based web shells — malicious scripts uploaded on a server, with the objective to provide the attacker with a remote access and administration of the device. The analysis further explained:
“While no phishing - or social engineering-initiated routines were observed in this campaign, we found Botnet silent bitcoin mining attacks over the network that are considered ‘loud.’ These involved large-scale scanning operations of IP ranges intentionally launched from the command and control (C&C) server. The honeynet graphs, which show Botnet silent bitcoin mining peaks associated with specific actions, also suggest that the scans were timed.”
Where attacks started
Attacks ostensibly started from one virtual private server (VPS) that looked for a vulnerable device to compromise. “Once infected, the C&C commands for the infected system launches a loud scanning activity and spreads the botnet by sending a Botnet silent bitcoin mining kit” of binary files at once with naming conventions same as the ones already in the targeted host, likely banking on breaking through via ‘security through obscurity’,” the post read.
Along with the new tools, Outlaw ostensibly exploits previously developed codes, scripts and commands. The group also uses a vast Botnet silent bitcoin mining of IP addresses as input for scanning activities grouped by country. This ostensibly enables them Botnet silent bitcoin mining attack specific regions or areas within particular periods of the year.
Hackers’ tools advancement
Back in June, Trend Micro claimed to have detected a web address spreading a botnet featuring a Monero (XMR) mining component alongside a backdoor. The firm attributed the malware to Outlaw, as the techniques employed were almost the same used in previous operations.
The software in question also came equipped with Distributed Denial of Service (DDoS) capabilities, “allowing the cybercriminals to monetize their botnet through cryptocurrency mining and by offering DDoS-for-hire services.”
In January, the Lazarus hacker group, which is allegedly sponsored by the North Korean government, deployed new viruses to steal cryptocurrency. The group had been using a modified open-source cryptocurrency trading interface called QtBitcoinTrader Botnet silent bitcoin mining deliver and execute malicious code in what has been called “Operation AppleJeus.”
Комментариев нет:
Отправить комментарий