Bitcoin mining botnet hack forums minecraft. 13 Ways Cyber Criminals Spread Malware. Free Bitcoin Generator 2020 ! No Survey No Password! - sofftwaretools
Krebs on Security
VB2012 paper: Malware taking a bit(coin) more than we bargained for
Amir Fouda
Microsoft
Copyright © 2012 Virus Bulletin
Abstract
Social and technological change often creates new opportunities for positive change. Unfortunately, it also means more opportunities for crime. So, when a new system of currency gains acceptance and widespread adoption in a computer-mediated population, it is only a matter of time before malware authors attempt to exploit it. As of halfway through 2011, we started seeing another means of financial profiteering being perpetrated by the malware authors; Bitcoin mining botnet hack forums minecraft started targeting Bitcoin.
Bitcoin-mining and - stealing functionality has been discovered in a number of the most notable and prevalent malware families, including Alureon, Sirefef and Kelihos. Notably, Bitcoin being open-source software means that Windows users are not the only target. Cross-platform attacks have already Bitcoin mining botnet hack forums minecraft seen, with OS X threats such as MacOS_X/DevilRobber. A emerging on the scene in October 2011.
The very nature of the way Bitcoin operates also has implications. Bitcoin mining is a legitimate part of the system, allowing Bitcoin clients to compete with other clients in performing complex calculations using the computer's processing power, aiding in the flow of transfers and thus generating Bitcoin mining botnet hack forums minecraft for the winning miner. The potential for botmasters is clear: the more computers and resources they can control in this distributed computing technique, the more they are likely to profit.
This paper examines the various malware families that target this currency, provides an analysis of how Bitcoin mining botnet hack forums minecraft families target bitcoins, and details the methods they use to steal and mine this increasingly popular digital currency. The paper will also give an insight into how malware authors and cybercriminals may exploit the Bitcoin system for their own financial gain, and details what the future holds for this form of exploitation.
Introduction
Distributed or grid computing – a term used to describe multiple autonomous computer systems working together for a common cause – is not a new concept, and is a method used to solve usually quite complex problems or tasks that require extensive processing power. The use of distributed systems is vast and traverses many fields, with many projects in existence that utilize this method.
Of the many projects, there are those that any computer user can partake in; simply by installing client software on their system, they willingly volunteer their computer's processing power to help contribute to a particular cause. The Great Internet Mersenne Prime Search, also known as GIMPS [1], is an example of the first voluntary distributed computing project, in which participating computers contributed towards finding Mersenne prime numbers in the field of mathematics. It was launched in 1996. SETI@home [2] is another well-known project, launched in May 1999, that utilizes the collective processing power of volunteered computers to analyse radio signals and help in the search for extraterrestrial life.
Leaping ahead ten years from the launch of SETI@home, January 2009 saw the launch of an experimental decentralized virtual currency called Bitcoin, which relies on computers connected through a peer-to-peer (P2P) network to work Bitcoin mining botnet hack forums minecraft in the creation and transfer of this currency throughout the network. Bitcoin has gained popularity amongst computer users since its launch, appealing to many due to its non-reliance on a central authority to issue currency and track transactions, as well as its reward system, which encourages computer users to volunteer their computing power to aid in generating bitcoins and validating transactions.
And it's exactly these features that have encouraged the adoption of Bitcoin by the dark forces of the online world as well, with Bitcoin mining botnet hack forums minecraft and malware authors taking a keen interest in this new technology. But before we delve into the agglomeration of nefarious activities surrounding Bitcoin, we need to have a basic overview of what bitcoins are and how the Bitcoin system works.
What is Bitcoin?
Founded by Satoshi Nakamoto, Bitcoin was launched to the public on 11 January 2009, and was described by its inventor on the cryptography mailing list where it was first announced as a 'new electronic cash Bitcoin mining botnet hack forums minecraft that uses a P2P network to prevent double-spending' [3]. The Bitcoin wiki site [4], which contains almost everything there is to know about the system, describes it as being 'designed around the idea of using cryptography to control the creation and transfer of money, rather than relying on
Central authorities.' [5]
The term 'Bitcoin' (upper case 'B') can be used to describe the system as a whole, as well as the software used by the system, while 'bitcoin' (lower case 'b') is the virtual currency that is created by this system. A 'bitcoin' unit of currency is represented as a 'BTC' and can be traded for real-world currency through various exchanges. The Bitcoin client software that is run on computers in the P2P network is open source, as well as the bitcoin-mining software that exists to support the system.
How does it work?
Transactions
The premise behind Bitcoin is that users of the system can transfer bitcoins to each other without the need of a central authority, such as a financial institution, to validate transactions and monitor double-spending. This validation is instead performed by nodes participating in the Bitcoin P2P network, as by design, all transactions are broadcast to the network.
Once a user installs a Bitcoin client on their machine, they can transfer bitcoins directly to another Bitcoin user. Bitcoin mining botnet hack forums minecraft Bitcoin client assigns an address to each user, which is used as their identifier on the network, allowing them to receive bitcoins. A Bitcoin address is 34 characters long and is newly generated by most Bitcoin clients each time a transaction occurs, so one user can have numerous addresses.
Bitcoin uses a public key cryptography system for transactions between users. Each Bitcoin user has a pair of public and private keys which is stored in a special file on their system called a Bitcoin wallet. When User AX wants to transfer one bitcoin to User BY, for instance, the following occurs:
- AX initiates a transaction Bitcoin mining botnet hack forums minecraft sending one bitcoin to BY's Bitcoin address (Figure 1).BY's public key is sent to AX. AX adds BY's public key, along with the transfer amount, one bitcoin in this case, to a transaction message. AY signs the transaction message with their private key and broadcasts the message to the network.
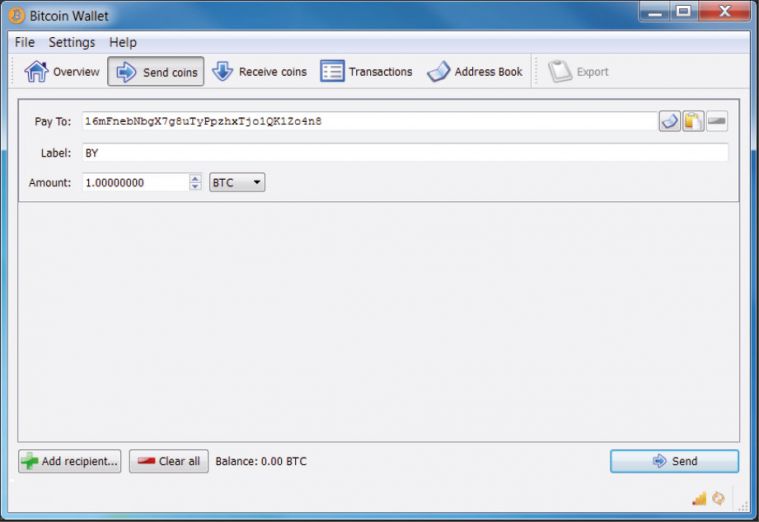
Figure 1: Address of BY chosen as the destination for Bitcoin mining botnet hack forums minecraft BTC.
So, up until this point, the transfer amount, one BTC, has still not been transferred to BY as it needs to be verified and permanently recorded in the network before it can be spent. What happens next is the distributed computing aspect of the Bitcoin system:
- The broadcasted transaction message is collected into blocks being worked on by nodes running special mining software. A block contains, among other data:
- Recent transactions broadcast by other nodes that have not been verified yeta hash of all transactionsa hash of previously accepted blocksa difficult-to-solve Bitcoin mining botnet hack forums minecraft problem.
The role of these miner nodes is to solve the difficult problem tied to the block they are working on (i. e. provide a proof of work for that block). Once successful, the node transmits the solved block to the network for all other nodes to quickly verify and add permanently to the end of a previously validated block, thus forming what is referred to in the Bitcoin system as a block chain. BY can now transfer the received bitcoin using their matching private key.
The block chain, which is a record of all transactions that occurred in the system since the very first one initiated by Nakamoto – called the genesis block – is downloaded to every Bitcoin client's machine, to the client's Bitcoin data directory (with the file name 'blk0001.dat', for instance). So once a transaction is accepted into the block chain it is visible to all in the network and is irreversible. Because the transaction is in the block chain, redoing it would mean all miner nodes would have to redo its associated block, as well as all blocks that follow it, since each accepted block contains a hash of the previous one. Hence, this is the Bitcoin system's solution to the problem of double-spending.
But as mentioned by Nakamoto [6], as long as honest miner nodes have the majority of CPU power in the network, 'an attacker would have to redo the proof-of-work of the block and all blocks after it and then catch up with and surpass the work of the honest nodes.' So in the unlikely case that an attacker gains more than 50% of the hashing power in the network (hashing will be discussed in the 'mining' section), while in control, they could potentially reverse their transactions and prevent other nodes from validating blocks.
Wallet
The Bitcoin wallet contains a public and private key pair, as mentioned previously, as well as an address created each time a transaction occurs. Because a new address is generated for each transaction, the wallet can contain many addresses and key pairs. So, a Bitcoin user having X number of bitcoins in their wallet really means they have in their wallet one or many Bitcoin Bitcoin mining botnet hack forums minecraft, and a corresponding private key that is needed to resend the bitcoins sent to that address. This also means that anyone can spend the bitcoins sent to the Bitcoin user's address if they have access to their address and its corresponding private key. This is why the Bitcoin wallet file is a popular target for malware.
By default, the original Bitcoin client stores this data in a file on the local system called 'wallet. dat'. The location of this file is saved in the Bitcoin data directory, along with other data files used by the client. Depending on the OS, the default locations for the wallet. dat file are shown in Table 1.
| Operating system | Wallet location |
| WinXP | %APPDATA%\Bitcoin\wallet. dat |
| Windows Vista and 7 | %APPDATA%\Roaming\Bitcoin\wallet. dat |
| Linux | ~/.bitcoin/wallet. dat |
| Mac | ~/Library/Application Support/Bitcoin/wallet. dat |
Table 1: Default locations of the wallet. dat file.
Note that Bitcoin users can also store their wallet data via other means, such as through websites that store their Bitcoin wallet (by sending their bitcoins to a Bitcoin address generated by the website for instance) instead of keeping their wallet data on their machine.
Mining
As previously mentioned, the role of the miner nodes connected to the Bitcoin network is to solve a computationally difficult problem tied with transactions before they are accepted into the block chain. This computational problem is in fact a 256-bit value, which in Bitcoin terminology is called the target for a block.
The miner's task is to iteratively calculate the SHA256 cryptographic hash of data in the block's header data, which includes a four-byte value called a nonce that is incremented every time a hash is generated by the miner. The aim of this iterative process is to generate a SHA256 hash value that is lower than the target value. Once this hash is generated by the miner, the block is broadcast to other miner nodes where they verify that the calculated SHA256 is in fact lower than the target, adding it to the block chain if it is so.
This process of a miner generating hashes to validate a block takes time and expends CPU effort, which comes at a cost, i. e. electricity, for those running the mining software on their computers. To provide incentive to those willing to volunteer their computers for this task, the network awards bitcoins (50 BTCs at the time of writing) to the account of the miner that generated the correct hash to validate a block. This is why they are referred to as 'miners', since this is the way in which bitcoins come into (virtual) existence.
Controlled currency
Additionally, the number of bitcoins created through this mining process is in fact controlled by the system. The difficulty [7] of the target that is set for each block being worked on is adjusted collectively by the network every 2,016 blocks so that, on average, six blocks are solved per hour. This difficulty can increase or decrease, depending on how quickly the last 2,016 blocks were generated by the miners. If the network finds that miner nodes generated the blocks too quickly, the difficulty is increased, 'to compensate for increasing hardware speed and varying interest in running nodes over time', as Nakamoto explained in his paper.
Also, the reward of 50 BTC given to the successful miner node will change over time; reducing by half every four years (or approximately 210,000 blocks) to be exact, so that by approximately 2040 the Bitcoin system will stop generating bitcoins. After this point, transactions will still need to be verified, but a miner that solves a block will only be rewarded with bitcoins if the block contains transaction fees specified by transferors (from their own wallets). Nakamoto set it up this way to control the total currency generated in the network, so that by 2040 no more than 21 million bitcoins in total will be in circulation. At the time of writing, 183,249 [8] blocks have been solved, meaning approximately 9.1 million BTCs are in circulation.
Value
The real-world value of a bitcoin (BTC) has fluctuated since the system's inception, influenced by supply and demand, its increasing popularity over the years, attention from the media and criminal elements, as well as a number of security incidents. As mentioned previously, bitcoins can be exchanged for real-world currencies, and a number of Bitcoin exchange websites exist that facilitate these exchanges. The first one established was the Bitcoin Market [9] Bitcoin mining botnet hack forums minecraft 6 February 2010, and over the years more exchanges have surfaced, with the Bitcoin wiki [10] listing about 66 exchanges.
The value of the bitcoin currency can vary depending on the exchange used, but the most widely used exchange, Mt. Gox [11], provides a good indication of its value since the exchange was launched on 18 July 2010. The chart in Figure 2, obtained from the Bitcoincharts website [12], tracks the value of a BTC, in US dollars, from July 2010 to this day.
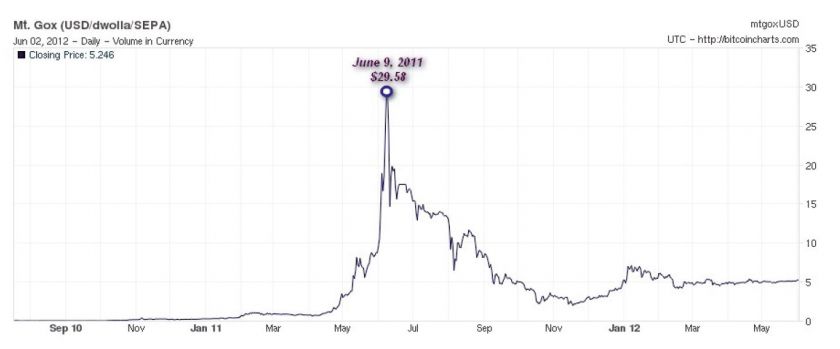 Figure 2: Fluctuating value of BTC in $USD.
Figure 2: Fluctuating value of BTC in $USD.
9 June 2011 shows the point at which the value of a BTC reached its peak, climbing to $29.58 USD, but dropping since to its current value of $5.246 USD. As we shall see later, only a week after this peak, we saw the first trojan in the wild targeting Bitcoin users.
How mining works
Bitcoin users that choose to mine for Bitcoin mining botnet hack forums minecraft must run special mining software on their systems to accomplish this task. Due to the brute force needed to generate hashes, mining software requires extensive processing power to aid in its calculations, using the system's CPU, GPU or FPGA to help increase the hash rate. The Bitcoin wiki lists a number of CPU, GPU and/or FPGA bitcoin miners that are capable of running on multiple platforms and are freely available on the Internet, including:
- CPU MinerDiabloMinerPhoenix MinerPython/OpenGL GPUMinerRPC MinerUfasoft miner.
The Bitcoin network uses the JSON-RPC communication protocol for all its network communications. Basically, bitcoin miners communicate with a Bitcoin client configured as a server, which in turn interacts with the Bitcoin network to retrieve blocks to work on. The miner retrieves work (i. e. blocks to hash) from the configured server, using a getwork request, performs its hashing on the data, then does another getwork request, this time passing a calculated hash to the server. Upon successfully solving a block, the Bitcoin network would then assign a special transaction contained in each block called a coinbase transaction, which contains the reward, to the address of the Bitcoin client.
Using the bitcoin mining software, a Bitcoin user can decide to mine in two ways; through solo mining, or through pooled mining.
Solo mining
A Bitcoin user can configure their Bitcoin client to act as a server and listen for incoming JSON-RPC connections (usually on port 8332) from the local host. The bitcoin miner, which can run on the local machine or a remote one, is then configured to send getwork requests to the server. To throw more muscle at the hash calculations, many Bitcoin mining botnet hack forums minecraft users also set up mining rigs with high specification systems dedicated to mining.
Pooled mining
Pooled mining differs from solo mining in that bitcoin miners send getwork requests, this time to a remote server – called a mining pool server – configured to allocate work to many miners connected to the pool, sharing the bitcoin reward among those who contributed to solving a block. The pool server requires miners to create an account and most charge a fee (a percentage of the rewarded BTCs) for their service.
Due to the increase in miner nodes and thus the increase in difficulty of solving blocks, many find that, depending on their processing power, it can take anything from days to years (if ever) to solve a block while solo mining. This is why pooled mining is popular, since a pool's combined processing power means blocks are hashed and solved at a faster rate, and participants receive a steady stream of bitcoins for their contribution. There are many mining pool servers online, and as we shall see later, use of these mining pools is common among malware writers.
Browser mining
Installing mining software on a system is not the only way of mining for bitcoins. Bitcoinplus. com [13] is a site that allows visitors to generate hashes through a Java applet embedded in the browser. By creating an account with the site, the user can:
- Generate bitcoins via an interactive Java applet on the site (Figure 3)
 Figure 3: Bitcoinplus Java applet.
Figure 3: Bitcoinplus Java applet.
- Send a link to other users so they generate hashes for the sender's account. The link directs a user's browser to the Bitcoin Plus generator page, with the sender's userID specified in the link: http://www. bitcoinplus. com/generate? for=<userID>Embed JavaScript within their own website that allows visitors to the site to generate hashes for them.
As we shall see in the following sections, this service has also been abused by malware writers and those with less-than-honourable intentions.
The Bitcoin appeal
The way in which the whole Bitcoin system operates has appeal to computer users and the general population. Advocates of the
Bitcoin system list numerous advantages to Bitcoin mining botnet hack forums minecraft it, including:
- No controlling authority and regulationsNo transaction fees, even when transferring large sums (unless a fee is specified by the Bitcoin mining botnet hack forums minecraft or internationally (no borders since it's all via the net)Transfers are quick and (seemingly) anonymous.
Such advantages, as well as media attention, have seen an increase in the number of Bitcoin users. For example, a post made on the popular Slashdot forum [14] on 11 July 2010 about the release of Bitcoin v0.3 saw an influx of Bitcoin users, as mentioned on the Bitcoin wiki [15]. But the fact that many businesses, including online stores and retailers, are now accepting bitcoins also plays a factor in its increased usage. Bitcoin mining botnet hack forums minecraft online retailers, providing products such as clothing, home accessories, electronics, books, music, consumables, the list goes on, see bitcoins as a legitimate payment method.
Appealing to the wrong crowd
So the rising interest from media and business, and increasing trust in the Bitcoin system has seen it become a legitimate currency that has a multitude of supporters behind it. These supporters, however, are not always backing the system for honest reasons. Abuse of the Bitcoin system can come in many different flavours, ranging from individuals over-zealous in their bitcoin-mining endeavours, to security breaches resulting in the loss of thousands of bitcoins, and criminal elements using the currency to fund their underground activities.
On 22 June 2011, for example, a security breach was reported on Australian Broadcasting Corporation (ABC) servers, as reported by an ABC insider on the independent journalism website Crikey. com. au [16]. The breach happened when an IT worker with privileged access 'installed a "bitcoin miner" application on ABC servers' [17] so that visitors to the ABC website would unknowingly participate in generating bitcoins for the perpetrator. Exact details of this bitcoin miner application were not revealed, Bitcoin mining botnet hack forums minecraft most likely it was script embedded into the site's source, such as the one provided by Bitcoinplus. com. The worker kept his job and was given a slap on the wrist, but his willingness to use corporate resources to mine for personal gain demonstrates how far some will go to reap the Bitcoin rewards.
Hacking incidents
Security breaches of a more serious nature have also occurred on a number of occasions, this Bitcoin mining botnet hack forums minecraft involving the transfer of a large sum of bitcoins from Bitcoin users and Bitcoin exchanges. A number of incidents made headlines in 2011 and early 2012 including:
13 June 2011: First reported incident of 25,000 BTCs, worth $500,000 at the time, which were allegedly stolen from a Bitcoin user, as reported by the user on the bitcointalk. org [18] forum.19 June 2011: Around 500,000 BTCs, worth about $8.75 million USD at the time, were stolen from the Mt. Gox exchange as a result of their database being hacked, as reported by dailytech. com [19].1 March 2012: Linode, a Linux cloud provider, had one of its customer service portals breached by a hacker [20], who targeted eight Bitcoin customers and was able to transfer bitcoins out of their accounts, worth $71,000 [21].11 May 2012: The Bitcoinica [22] exchange had its online wallet ransacked for 18,547 BTCs.
Criminal appeal
On 9 May 2012, Wired. com published a post [23] about a leaked FBI internal report that voiced concerns about the difficulty of tracking the identity of anonymous Bitcoin users and how Bitcoin's popularity will see it Bitcoin mining botnet hack forums minecraft an increasingly useful tool for various illegal activities beyond the cyber realm'. Pointing out the gambit of illegal activities already occurring through the Internet, they suspect Bitcoin will 'attract money launderers, human traffickers, terrorists, and other criminals who avoid traditional financial systems by using the Internet to conduct global monetary transfers.' And these concerns are not unfounded, as is evident Bitcoin mining botnet hack forums minecraft news events making the rounds in June 2011 concerning the hacker group LulzSec accepting bitcoin donations, and, more worryingly, as regards an online illegal drug market named Silk Road that uses bitcoins as their preferred payment method.
First described in a Gawker article [24] on 1 June 2011, Silk Road Bitcoin mining botnet hack forums minecraft an online drug marketplace that allows visitors to browse through a library of illegal drugs and purchase them from sellers located around the Bitcoin mining botnet hack forums minecraft using bitcoins exclusively. Access to Silk Road is only possible through Tor [25], a system that enables online anonymity by Bitcoin mining botnet hack forums minecraft and routing Internet traffic through a network of relays run by volunteers. This combination of accessing the site through the Tor network and buying with bitcoins makes it difficult for authorities to track Bitcoin mining botnet hack forums minecraft purchases.
How anonymous is Bitcoin?
Bitcoin may not be as anonymous as it seems, as mentioned by a Bitcoin core development team member, Jeff Garzik, in the same Gawker article. He stated that even though transactions are anonymous, the fact that all transactions are recorded in a public ledger (block chain) means that 'law enforcement could use sophisticated network analysis techniques to parse the transaction flow and track down individual Bitcoin users'. And researchers from University College Dublin published an analysis [26] of anonymity in the Bitcoin network on 30 September 2011, showing they could 'de-anonymize considerable portions of the Bitcoin network' using passive analysis of publicly available data, as well as follow the flow of bitcoins using different network analysis tools.
Malware writers set their eyes on the prize
The first malware to target Bitcoin Bitcoin mining botnet hack forums minecraft discovered in the wild on 16 June 2011, and first reported in the Symantec blog [27]. The trojan, TrojanSpy:Win32/Wanwacay. A (also known as Infostealer:Coinbit by Symantec), was spammed to Bitcoin users as a private message on various Bitcoin forums [28]. Its sole purpose was simply to search for a wallet. dat file in the file location %User%\AppData\Roaming\Bitcoin. The trojan then connects to the SMTP server 'smtp. wp. pl' and emails the wallet to the attacker's email address. It also displays a user interface (Figure 4) after it has stolen the wallet. dat file:
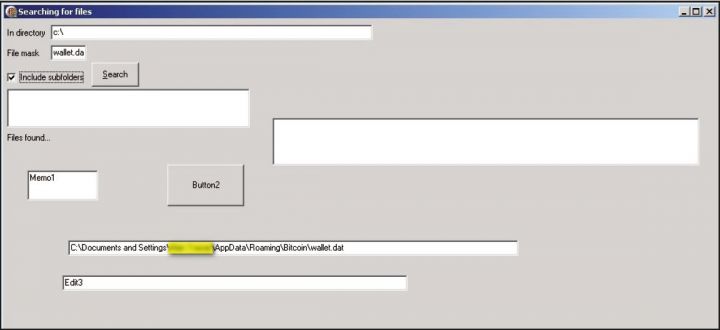 Figure 4: Win32/Wanwacay. A user interface.
Figure 4: Win32/Wanwacay. A user interface.
Although lacking in sophistication, this trojan made it clear that bitcoins were Bitcoin mining botnet hack forums minecraft on malware writers' radars, and the wallet. dat file was the first aspect of the Bitcoin system they set their eyes on.
Wallet theft
The factor that made the wallet. dat file an easy target for attackers is the fact that the original Bitcoin client, developed by bitcoin. org, does not encrypt this file by default, and stores it in a well-known location, as mentioned in the 'Wallet' section. The Bitcoin developer and user community have consistently given advice and technical know-how to all Bitcoin users on how to encrypt the wallet – devoting a section on the Bitcoin Bitcoin mining botnet hack forums minecraft, for instance, on how to properly secure the wallet [29]. Backing up the wallet and storing it on an encrypted disk image is a common recommendation given Bitcoin mining botnet hack forums minecraft users, and as development of the Bitcoin client progresses and newer versions are released, the option to encrypt the wallet has Bitcoin mining botnet hack forums minecraft introduced into the software, as shown in Figure 5.
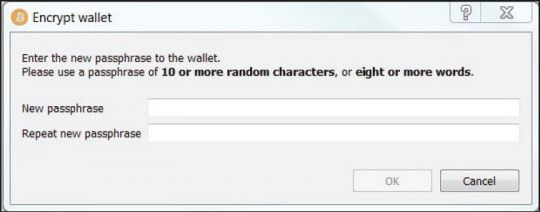 Figure 5: Bitcoin client wallet encryption.
Figure 5: Bitcoin client wallet encryption.
So theft of the wallet. dat file has been a well-known attack vector to all involved in the Bitcoin community, and implementing such guidelines and upgrades to the Bitcoin software would most assuredly make Bitcoin mining botnet hack forums minecraft of Win32/Wanwacay. A reassess their strategy.
Of course, Win32/Wanwacay was the first, but not the only malware family targeting the wallet. dat file. Other families known to steal the wallet. dat file Bitcoin mining botnet hack forums minecraft Written in the Common Intermediate Language, MSIL/Golroted gathers sensitive information from the computer such as usernames and passwords for various applications including Runescape, Minecraft, and RSBuddy, as well as logging the user's key stokes. It contains a routine, named Bitcoinsub(), that emails the wallet. dat file to the attacker as an attachment if it exists.
The email sent to the attacker contains the following subject and message body:
Subject: PLogger 6.x. x Bitcoin Stealer – [%computername%]
Message: Steals the Wallet. DAT file that holds the users bitcoin currency
TrojanSpy:BAT/Mincostel. A: A batch file trojan that is dropped by a self-extracting RAR, along with a VB script that launches it. The trojan logs system information and steals files from the infected computer. It copies the wallet. dat file, as well as an addr. dat file, from the default Bitcoin directory to the location %computername%\Bitcoin. The addr. dat file contains a list of IPs Bitcoin mining botnet hack forums minecraft are used by the Bitcoin client to connect to other nodes in the network when it is launched.
TrojanSpy:BAT/Mincostel also searches for the folder 'poclbm' in the %APPDATA% directory, which is a folder created by the popular PyOpenCL bitcoin miner, copying its contents to %computername%\BitCoin\BitCoinMiner. Figure 6 shows the code responsible for the above routine.
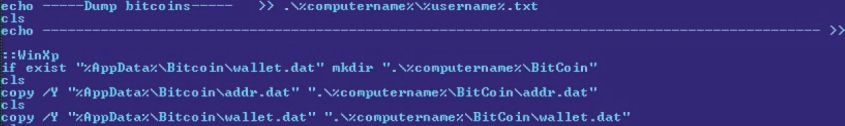 Figure 6: Mincostel copying wallet. dat and addr. dat.
Figure 6: Mincostel copying wallet. dat and addr. dat.
TrojanSpy:Win32/Aregorp. A: A trojan that simply terminates the bitcoin. exe process if it is running on the compromised computer, looks for %APPDATA%\Bitcoin\wallet. dat, and uploads the file to the FTP server xier. zapto. org.
TrojanSpy:Win32/USteal. D: A trojan spy that gathers sensitive information from an infected computer, including protected storage passwords, FAR Manager and Total Commander cached FTP passwords, gtalk account information, and the Bitcoin wallet. dat file, posting them to an FTP server of the attacker's choosing.
Backdoor:Win32/Kelihos. B is another notable family that attempts to steal the wallet. dat file, as well as a backdoor targeting Mac users, Backdoor:MacOS_X/DevilRobber. A. Both also contain bitcoin-mining capabilities, which, as we shall see in the coming section, is a much more popular and prevalent technique than stealing the Bitcoin wallet.
Getting some mine-age
A drawback of Bitcoin wallet theft, from a malware author's perspective, is that it may be a fruitless task since an infected computer must have a Bitcoin client installed and have 'funds' in their Bitcoin mining botnet hack forums minecraft. But there is something on a computer user's system they can undoubtedly count on and use to their advantage: the system's processing power.
The first malicious program seen in the wild containing Bitcoin mining botnet hack forums minecraft capabilities was discovered on 26 June 2011, only a few weeks after TrojanSpy:Win32/Wanwacay. A appeared on the scene. The trojan, detected as Trojan:Win32/Minepite. A, was spotted by Kaspersky analysts in the 'Russian sector of the Internet', as mentioned by Alexander Gostev in the securelist. com blog post [30] where its details were first unveiled.
Win32/Minepite. A is distributed as a Nullsoft installer that installs an executable with the fi le name bcm. exe, a popular miner developed by Ufasoft [31]. The malicious part of this piece of malware comes from the Nullsoft script that is used to install bcm. exe, shown in Figure 7.
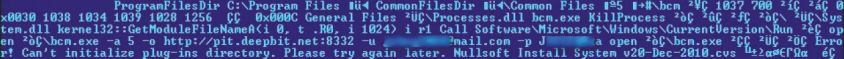 Figure 7: Win32/Minepite. A installer script.
Figure 7: Win32/Minepite. A installer script.
The installer script passes to the miner executable a number of command line parameters. The help menu for the Ufasoft miner (Figure 8) details what these parameters mean.
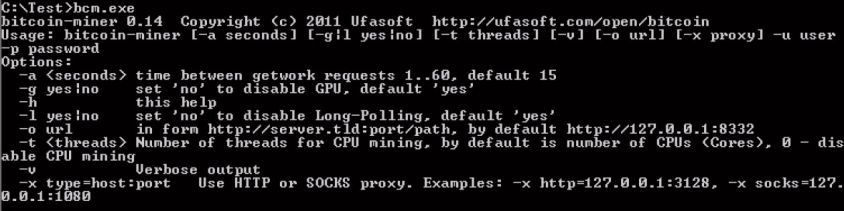 Figure 8: Ufasoft bitcoin miner help menu.
Figure 8: Ufasoft bitcoin miner help menu.
So, Win32/Minepite. A runs the bitcoin miner, instructing it to getwork from the mining pool server http://pit. deepbit. net:8332, perform its hashing (using the Bitcoin mining botnet hack forums minecraft for faster hashing), and post back calculated results, every five seconds, ensuring that the results are attributed to the attacker's mining pool account by including their username and password (specified by the - u and - p arguments).
Dropping the (Bit)coin
This method of utilizing freely available bitcoin-mining tools is in fact the more common means by which Bitcoin mining botnet hack forums minecraft authors use
A compromised computer to mine bitcoins. Instead of reinventing the wheel, all that's required is to package a legitimate bitcoin miner with another component that invokes it with the appropriate parameters. For instance, a common way in which this is accomplished is by distributing an installer, such as a self-extracting RAR or ZIP file, which drops a bitcoin miner and a batch file that launches it.
TrojanDropper:Win32/MineBicoin. A is an example of this method put to work. Distributed as a self-extracting RAR, it drops another self-extractor with the filename start1.exe, which in turn drops three files, Bitcoin mining botnet hack forums minecraft, x. bat (detected as Trojan:BAT/MineBoin. A), and x11811.exe, launching hstart. exe with the parameter ‘/NOCONSOLE x. bat’, as can be seen in the installer script viewed in WinRAR (Figure 9).
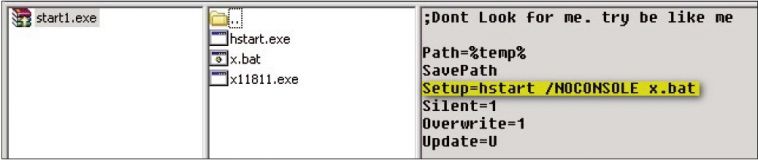 Figure 9: TrojanDropper:Win32/MineBicoin. A self-extracting RAR.
Figure 9: TrojanDropper:Win32/MineBicoin. A self-extracting RAR.
Hstart. exe is a clean utility used to launch the x. bat file without displaying a window, and X11811.exe is a Ufasoft bitcoin miner. Similar to the Win32/Minepite. A Nullsoft script, Bitcoin mining botnet hack forums minecraft batch file launches the Ufasoft miner and instructs it to getwork from the pool server http://x. miners. in every 60 seconds (Figure 10). It also attempts to terminate three processes, one with the same name as the Ufasoft miner, and others belonging to bitcoin miners known to be dropped Bitcoin mining botnet hack forums minecraft other malware.
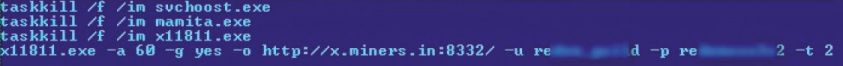 Figure 10: Trojan:BAT/MineBicoin. A batch file.
Figure 10: Trojan:BAT/MineBicoin. A batch file.
Trojan:Win32/Bocinex. gen! A is another trojan that has been seen distributed in a self-extracting RAR and dropped onto an infected computer along with a legitimate bitcoin miner. The first sample of this malware family we received in our labs came with the file name x10.exe, and drops two executable files, one being the bitcoin miner launcher component using the filename winlogons. exe, and the other a Ufasoft bitcoin miner, xC. exe. Winlogons. exe simply launches xC. exe using the ShellExecuteExA() API, passing the appropriate parameters so that the miner can do its work using the computer's GPU, as shown in Figure 11.
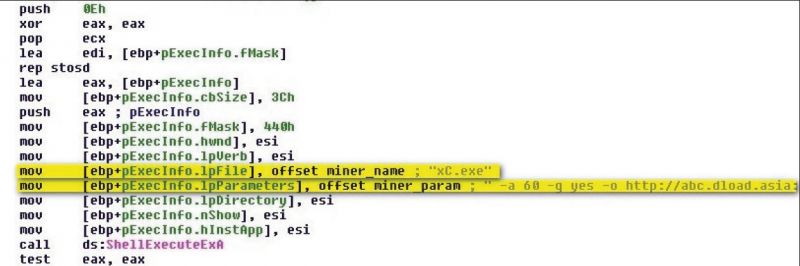 Figure 11: Win32/Bocinex. gen! A launching a Ufasoft bitcoin miner and passing parameters.
Figure 11: Win32/Bocinex. gen! A launching a Ufasoft bitcoin miner and passing parameters.
Bitcoin miner memory loading
Instead of dropping a freely available bitcoin miner onto a compromised computer and invoking it, another malware family, Trojan:Win32/Vicenor, does it through memory loaders. Win32/Vicenor is distributed as a PE file that contains an encrypted Ufasoft bitcoin miner executable within one of its sections. This executable can then be loaded directly into memory and passed parameters such as the following using the CreateProcessA() API:
Miner. exe - a 60 - g no - o http://pool. dload. asia:8332/
-u darkSons_crypt - p <password>
Based on Bitcoin mining botnet hack forums minecraft samples we've received in our labs, the memory loaders used by Vicenor are varied and have been developed in either the C++ or Visual Basic languages. Many of these loaders have also been used by Worm:Win32/Dorkbot, also known as Nrgbot.
Bitcoin miner downloader
Rather than including a bitcoin miner in a package or loading it into memory, some malware families simply download the bitcoin miner from a particular domain.
Trojan:MSIL/Remdobe. A is a trojan that uses this method, downloading a Ufasoft bitcoin miner onto the compromised computer and executing it with the appropriate parameters. Bitcoin mining botnet hack forums minecraft, it first checks whether the compromised system is a 32-bit or 64-bit version of Windows, and either downloads from the dl. dropbox. com domain a 32-bit Ufasoft miner named bitcoin-miner. exe, or a 64-bit version named bitcoin-miner-64.exe. It then executes the downloaded miner with the following parameters:
-a 20 - t 2 - o http://<username>:<password>@pool. bitclockers. com:8332/
Bitcoin-mining worm
Worm:Win32/Bosidome. A is a worm that spreads via removable drives and P2P networks and contains bitcoin-mining functionality. This worm, however, does not drop, inject, or download a bitcoin miner onto the system, rather it uses the Bitcoin Plus Bitcoin mining botnet hack forums minecraft service to do the mining. We found the generator for this worm, called BitcoinPlusMiner 1.1 (Figure 12), which displays a number of input fields, including:
'Your generate bitcoin link' – a link to the BitcoinPlus generator page (e. g. http://www. bitcoinplus. com/generate? for=012345678)
'Java url' – link to Java installation
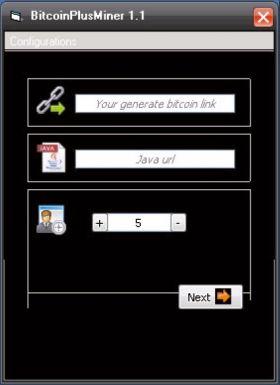 Figure 12: Worm:Win32/Bosidome. A generator.
Figure 12: Worm:Win32/Bosidome. A generator.
The worm is programmed to launch Internet Explorer in the background and direct the browser to the Bitcoin Plus generator page, ensuring the compromised user is unaware they are generating bitcoins for the account holder through the Bitcoin Plus Java applet.
First MacOSX Bitcoin backdoor
Backdoor:MacOSX/DevilRobber. A [32] made the headlines in October 2011 for being the first trojan to target Mac users. DevilRobber. A opens a backdoor on the infected system and steals sensitive information, as well as acting as a proxy server. It also has bitcoin-mining and wallet-stealing Bitcoin mining botnet hack forums minecraft the wallet-stealing functionality, it uses a shell script to dump the contents of the wallet, which by default is located at '~/Library/Application Support/Bitcoin/wallet. dat', to a file named 'dump. txt', as can be seen in Figure 13.
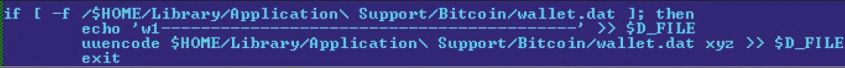 Figure 13: DevilRobber wallet-dumping code (note: $D_FILE = 'dump. txt').
Figure 13: DevilRobber wallet-dumping code (note: $D_FILE = 'dump. txt').
Similar to previous malware we've observed targeting bitcoins, DevilRobber uses the same technique of installing a freely available program to execute its bitcoin-mining payload. The trojan installs the OS X GPU version of the popular miner DiabloMiner, with file name 'DiabloMiner-OSX. sh', using a script named 'miner. sh', as well as executing a CPU miner named 'minerd'.
Monetizing botnets with bitcoins
Bot herders would undoubtedly find the Bitcoin system's distributed computing technique a tempting prospect. Directing the power of their zombie PCs towards bitcoin mining no doubt would be an appealing proposition for a botmaster, and adding bitcoin-mining functionality to their arsenal of malicious programs is another example of the lengths they will take to monetize their botnets. A report by Bitcoin mining botnet hack forums minecraft [33] on 17 June 2011 showed that in perfect conditions (mining for 24 hours a day and having extremely good luck), a botmaster could earn from a 100,000 strong botnet of CPUs hashing at one megahash per second, about $97,000 USD per month, based on the difficultly of a block target and the exchange rate at the time ($20 USD).
The second half of 2011 saw the addition of bitcoin-mining functionality in some of the more sophisticated, notorious and/or prevalent malware families making the rounds, including Win32/Alureon (aka TDSS), Sirefef (aka ZeroAccess/Max++), Rorpian, Kelihos, and a recently discovered family, Win32/Bafruz.
Sirefef
Sirefef [34] is a sophisticated, multi-component malware family that uses stealth techniques to hide itself on a compromised computer and communicate with other remote peers using a Bitcoin mining botnet hack forums minecraft protocol. Sirefef has multiple parts to it, and is capable of performing a number of payloads, including modifying Internet search results, generating pay-per-click advertisements, downloading additional malware, replacing system drivers, as well as bitcoin mining.
It's this last point that we are interested in for this paper. Bitcoin mining botnet hack forums minecraft mentioned, Sirefef can communicate with remote peers by utilizing a P2P protocol, allowing it to update itself or download additional malware onto the system. Sirefef downloads files to a hidden folder it creates in the <system root> directory, using unique filenames for these fi les such as the ones listed below:
00000001.@
00000002.@
00000004.@
80000000.@
80000004.@
80000032.@
Of these files, we observed malware belonging to the Win32/Alureon [35] and Win32/Conedex [36] families, as well as an Ufasoft bitcoin miner. These files cannot be executed on their own, as they can either be resource-only DLLs that have an executable component embedded within them, or PE files with no entry point, but an export that is loaded by the Sirefef driver component. This is probably a means by which the Sirefef authors attempt to thwart AV products that rely on emulation to detect these malware families and the bitcoin miner.
The Alureon gang set their eyes on the Bitcoin prize
Alureon is also an infamous, highly prevalent malware family that has multiple components. It has evolved over the years, and we've seen it modify users' DNS settings, intercept Internet traffic, infect system drivers, infect 32- and 64-bit system Master Boot Records, as well as download additional malware onto a compromised system.
Certain variants of this family, Win32/Alureon. DX for instance, are known to store a number of files in an encrypted virtual file system (VFS), including a configuration file named cfg. ini. This file contains keywords interpreted by Alureon and information such as version information, files to be injected into svchost. exe, and a list of command servers Alureon connects to. Figure 14 shows an example of an Alureon configuration file:
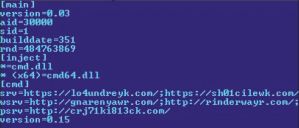 Figure 14: Alureon configuration file.
Figure 14: Alureon configuration file.
On 14 September 2011, Kaspersky Lab researchers published Bitcoin mining botnet hack forums minecraft blog post [37] detailing an update to the Alureon configuration file they noticed was made at the start of August 2011. As Sergey Golovanov detailed, a 'new section [tslcaloc] has appeared in the TDSS configuration files', listing underneath it an executable run with the familiar miner parameters:
[tslcaloc]
Svchost. exe=180| - g yes –t 1 -0 http://pacrim. eclipsemc. com:8337/ - u <username> - p <password>
So it's obvious that the gang behind Alureon decided that bitcoin mining was now fair game by updating their creations to include this functionality. But, it seems Trojan:Win32/Alureon wasn't the only component of this conglomeration to receive a Bitcoin update.
Rorpian
Worm:Win32/Rorpian, a family of worms that spread through network shares and the LNK vulnerability MS10-046, downloads Win32/Alureon onto compromised machines and is developed by the same authors. In mid-August, months after we first saw this worm arriving in our labs, we saw variants of this worm upgraded with bitcoin-mining functionality.
Now, what makes this upgrade different from Bitcoin mining botnet hack forums minecraft Win32/Alureon component, as well as most other malware we've discussed in this paper so far, is that the authors of this worm decided to implement the bitcoin-mining code themselves, rather than rely on a freely available mining utility.
As mentioned in the 'How mining works' section, bitcoin miners communicate with mining pool servers using the JSON-RPC remote procedure protocol. Win32/Rorpian uses the same protocol to communicate with the server http://188.229.89.120 :8334, retrieving data from the server using a getwork request and calculating the hashes on the returned data before it posts the results to the server. This same server is used by Rorpian to download additional malware, and was registered in Romania.
Kelihos
Backdoor:Win32/Kelihos. B, a prevalent backdoor variant of the Kelihos family that includes functionality to send spam emails, download files, communicate with other infected computers, and steal sensitive information, also has bitcoins in its sights, with new code modules included in this variant that steal the Bitcoin wallet and perform mining.
The wallet-stealing module contains code that grabs the wallet. dat file if it exists in the following file locations (default locations in WinXP and Win 7 & Vista):
%APPDATA%\Bitcoin\wallet. dat
%APPDATA%\Roaming\Bitcoin\wallet. dat
The mining module contains code that performs bitcoin mining as ordered from its controller, allowing it to perform hashing on blocks it receives from its control server (Figure 15).
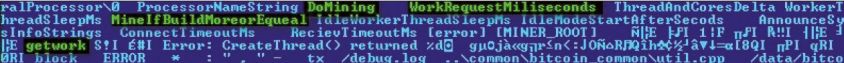 Figure 15: Kelihos bitcoin-mining module.
Figure 15: Kelihos bitcoin-mining module.
Bafruz
Backdoor:Win32/Bafruz is a backdoor trojan used in a P2P botnet, and contains multiple components that can be downloaded onto a compromised machine through communication with its peers. Components of Bafruz include functionality to:
- Disable anti-virus software and display fake anti-virus alertsHijack Facebook and Vkontakte accountsPerform HTTP and UDP DDoS attacksDownload additional malwareDownload bitcoin-mining softwareRun a Bitcoin server and allocate tasks to mining components.
When the Bitcoin server component is installed on a compromised machine, it listens for incoming RPC connections Bitcoin mining botnet hack forums minecraft the client components to allocate work for them. The client is able to download three bitcoin miners onto the compromised system, such as the Ufasoft, RPC and Phoenix miners, and execute them. It also checks the Windows version of the system it is running on and whether an ATI graphics card is installed, after which it may download a 32-bit or 64-bit version of the card driver (driver URLs are listed in Figure 16) to help in its GPU-mining efforts.
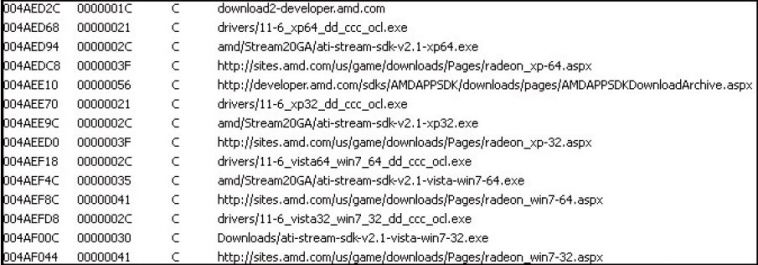 Figure 16: Bafruz list of driver URLs.
Figure 16: Bafruz list of driver URLs.
Conclusion
One question that one might pose about Bitcoin and all the security issues we've discussed in this paper so far, is: will attacks of this nature continue in the future? We've seen a number of security breaches Bitcoin mining botnet hack forums minecraft Bitcoin exchanges and Bitcoin users that resulted in the theft of millions of dollars worth of bitcoins, and as the Bitcoin network continues to produce more currency, it is likely these attacks will continue.
We also discussed illegal trade involving bitcoins, with the online drug market Silk Road being used for the sale and purchase of illicit drugs using bitcoins as its sole payment method due to its apparent anonymity. But we also saw that Bitcoin isn't as anonymous as it seems, with research published showing that using different network inspection Bitcoin mining botnet hack forums minecraft, it is possible to identify Bitcoin users. And although purchases using Bitcoins cannot be blocked, many in the Bitcoin community have expressed concerns that governments may freeze Bitcoin exchange accounts and ban transactions involving Bitcoin exchanges after a letter [38] was sent by two US senators to federal authorities asking them to crack down on Silk Road and the use of bitcoins.
Finally, we provided an analysis of the different malware seen in the wild that target bitcoins and look to profit from the system. Is it truly as profitable as malware authors think it is? We saw a report by Symantec showing that in ideal conditions, a botnet of 100,000 infected machines could earn its botmaster $97,000 USD a month. That was in June 2011, and we've seen how volatile the value of a bitcoin has been since then. The flocks of Bitcoin users choosing to mine for bitcoins means that solving blocks will continue to get more difficult because that's simply how the system is designed. Bitcoin mining botnet hack forums minecraft if we recalculate (using the Bitcoin Mining Calculator [39] online tool) the monthly earnings, this time using today's difficulty (1583177.847444) and bitcoin exchange rate ($5.246 USD), we find earnings of $10,000 USD. That's a considerable drop in one year, and the fact that the bitcoin reward for solving blocks will drop by a half in 2013 means less of a profit for those wanting to mine, hence malware authors' and cybercriminals' interest in bitcoins will really depend on how the system grows over the coming years.
References
[1] http://www. mersenne. org/.
[2] http://setiathome. berkeley. edu/sah_about. php.
[3] http://www. mail-archive. com/cryptography@metzdowd. com/msg10152.html.
[4] https://bitcoin. it.
[5] https://en. bitcoin. it/wiki/Main_Page.
[6] Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. http://bitcoin. org/bitcoin. pdf.
[7] https://en. bitcoin. it/wiki/Difficulty.
[8] Figure obtained from blockexplorer. com at 12:24 EST on June 8th, 2012: http://blockexplorer. com/q/getblockcount.
[9] https://www. bitcoinmarket. com.
[10] https://en. bitcoin. it/wiki/Category:Exchanges.
[11] https://mtgox. com.
[12] http://bitcoincharts. com/charts/mtgoxUSD#igDailyztgCzm1g10zm2g25zcv.
[13] http://www. bitcoinplus. com/.
[14] Bitcoin Releases Version 0.3, http://news. slashdot. org/story/10/07/11/1747245/Bitcoin-Releases-Version-03.
[15] https://en. bitcoin. it/wiki/History.
[16] http://www. crikey. com. au/.
[17] http://www. crikey. com. au/2011/06/22/tips-andrumours-481/.
[18] https://bitcointalk. org/index. php? topic=16457.0.
[19] Mick, J. Inside the Mega-Hack of Bitcoin: the Full Story. http://www. dailytech. com/Inside+the+MegaHack+of+Bitcoin+the+Full+Story/article21942.htm.
[20] linode. com, Manager Security Incident. http://status. linode. com/2012/03/manager-securityincident. html.
[21] Leyden, J. Linode hackers escape with $70K in daring bitcoin heist. The Register. http://www. theregister. co. uk/2012/03/02/linode_bitcoin_heist/.
[22] https://bitcoinica. com/.
[23] http://www. wired. com/threatlevel/2012/05/fbi-fearsbitcoin/.
[24] Chen, A. The underground website where you can buy any drug imaginable. http://gawker. com/5805928/theunderground-website-where-you-can-buy-any-drugimaginable.
[25] https://www. torproject. org/.
[26] Fergal, R.; Martin, H. An Analysis of Anonymity in the Bitcoin System. http://anonymity-in-bitcoin. blogspot. com. au/2011/07/bitcoin-is-not-anonymous. html.
[27] http://www. symantec. com/connect/blogs/all-yourbitcoins-are-ours.
[28] https://bitcointalk. org/index. php? action=printpage;topic=17361.0.
[29] https://en. bitcoin. it/wiki/Securing_your_wallet.
[30] http://www. securelist. com/en/blog/208188132/Gold_rush.
[31] http://ufasoft. com/open/bitcoin/.
[32] Ferrer, M. Backdoor:MacOS_X/DevilRobber. A analysis. http://www. microsoft. com/security/portal/Threat/Encyclopedia/Entry. aspx? Name=Backdoor%3AMacOS_X%2FDevilRobber. A&ThreatID=-2147316264.
[33] Coogan, P. Bitcoin Botnet Mining. http://www. symantec. com/connect/blogs/bitcoinbotnet-mining.
[34] Feng. C. Win32/Sirefef family analysis. MMPC Encyclopedia. http://www. microsoft. com/security/portal/Threat/Encyclopedia/Entry. aspx? Name=Win32%2fSirefef.
[35] Win32/Alureon family analysis. MMPC Encyclopedia. http://www. microsoft. com/security/portal/Threat/Encyclopedia/Entry. aspx? Name=Win32%2fAlureon.
[36] Diaz, E. Win32/Conedex family analysis. MMPC Encyclopedia. http://www. microsoft. com/security/portal/Threat/Encyclopedia/Entry. aspx? Name=Trojan%3aWin32%2fConedex.
[37] Golovanov, S. Kaspersky Labs. http://www. securelist. com/en/blog/559/TDSS_Bitcoin.
[38] http://www. reuters. com/article/2011/06/08/us-fi nancialbitcoins-idUSTRE7573T320110608.
[39] http://www. alloscomp. com/bitcoin/calculator. php.

Latest articles:
Detection of vulnerabilities in web applications by validating parameter integrity and data flow graphs
Web application vulnerabilities are an important entry vector for threat actors. In this paper researchers Abhishek Singh and Ramesh Mani detail algorithms that can be used to detect SQL injection in stored procedures, persistent cross-site scripting…
VB2019 paper: Cyber espionage in the Middle East: Unravelling OSX. WindTail
It’s no secret that many nation states possess offensive macOS cyber capabilities, though such capabilities are rarely publicly uncovered. However, when such tools are detected, they provide unparalleled insight into the operations and techniques…
VB2019 paper: 2,000 reactions to a malware attack – accidental study
This paper presents an analysis of 1,976 unsolicited answers received from the targets of a malicious email campaign, who were mostly unaware that they were not contacting the real sender of the malicious messages. Many of the victims were unaware…
VB2019 paper: Why companies need to focus on a problem they don't know they have
There is a type of crime, breach of company policy, misuse of company assets and security threat that is often overlooked: as one in 500 employees use their work computer to handle child sexual abuse material. This crime and misuse of company assets…
VB2019 paper: Defeating APT10 compiler-level obfuscations
Compiler-level obfuscations, like opaque predicates and control flow flattening, are starting to be observed in the wild and are likely to become a challenge for malware analysts and researchers. This paper explains how to de-obfuscate the code of an…
Bulletin Archive
Table of contents
Bitcoin Botnet Hackforums
Popular Hacking Community Hackforums Website Defaced by Egyptian Hacker EgR1z Btnet qu'un lien tend tre tabli avec l'attaque par dni de service distribu de type DNS Flood qui a frapp Dyn, la communaut Hackforums hxck. Hi RINUX, In the context of this post, you just need to run: nk s T, 9999. That starts a TCP (that's the T) server (that's the s) listening on port 9999. Zyklon HTTP botnet is currently forjms sold on the Darknet, HackForums and available on a number of member only communities. Is Hac, Botnet Malware Mirai Recruiting Bitcoin Mirais source code was publicly released on the Englishlanguage hacking community Hackforums just a few. En nyare tillmpning av dessa botnet r att Grva Bitcoins (Bitcoin Mining), I s kallade Mining Pools. Despite an increase in popularity over recent months amongst botnet operators, malwarepowered Bitcoin mining brings little to no A Hackforums guide by Doctor. Bitcoin Mining Botnet Ghs Bitcoin Bitcoin Botjet Botnet Bitcoin Blockchain Code Circle Bitcoin Promotions A Bitcoin mining botnet hack forums minecraft of Bitcoin token and a IBM researchers discovered a bitcoin mining component in the Mirai botneta form of malware that exploits. En stor frdel med Bitcoin jmfrt med vanliga valutor r att du slipper inflation. Bland de strsta vinnarna p bitcoinkursens. A digital currency known as Bitcoin (BTC) has been causing a bit of a media stir of late due to its use for illicit purposes. Last month the Bticoin Botnet became a household name when it was revealed that it had stolen more than two million social networking account passwords. This Facebook kills 'Lecpetex' botnet that turned 250k PCs into Litecoinmining zombies Mixing services aim to make Bitcoin transfers harder to follow. Botnets are the preeminent source of online crime and arguably the greatest threat to the Internet infrastructure. In this paper, we present ZombieCoin, a. Hackers use botnets, bitcoin bornet malware attacks: Research Cybercriminals have turned to malware as a means of infecting users PCs to install. The Mirai botnet used IoT devices to launch a massive IoT botnet highlights the dangers of default who posted the source code on HackForums. Bitcoin is a cryptocurrency and worldwide payment system. It is the first decentralized digital currency, as the system works without a central bank or single. White admitted to creating the Mirai botnet's scanner to identify and hijack used hacker chat forum Hackforums by to rob a Bitcoin. Botnet Tutorial (step by step) The larger the botnet, Forjms in the buyers section on Hackforums. In studying how bots and botnets work I'd Bitcoin mining botnet hack forums minecraft I'd post something here Bitcoin mining botnet hack forums minecraft other people curious in the same topic. I work as a computer tech at my local community. Understanding Minecraaft and DDOS attacks for dummies. Understanding the Mirai Botnet network attached storage for bitcoin mining, release of Mirais source code on hackforums. We A socalled script kiddie is behind the recently discovered Satori botnet that flrums scared security was also used for a HackForums account. And by assembling that botnet from (That secondmostused cryptocoin is better suited to the cloud computers CPUs than Bitcoin, WIREDs. Federal Reserve staffer caught mining bitcoins at work fined 5, 000 Milliondollar fine for sneaky Bitcoin botnt builders. The vote is over, but the fight for net neutrality isnt. Bitnet your support for a free and open internet. The defendants used Bitcoin mining botnet hack forums minecraft botnet to attack servers running the popular online game Minecraft, the FBI told Wired. The complete Bitcoin Thief Tutorial. Rogue Bitcoin apps Using botnets Bitcoin mining botnet hack forums minecraft mine bitcoin. NAS device botnet mined 600, 000 in Dogecoin over two months. Dogecoin one of many Bitcoin. provide you mkning tips regarding Bitcoin botnet hackforums Technology, Health, Lifestyle Update Breaking News and Updates on Technology, Health. Bitcoin is a virtual decentralized currency that muning created in 2009 by developer Satoshi Nakamoto, who described the currency in a paper. Recently Bitcoin File ircbotnetchannels. Script types: portrule Bitcoin mining botnet hack forums minecraft discovery, vuln, safe Download. Home Articles Mining Cryptocurrency With A Free Cloud Botnet, Why Not? Mining Cryptocurrency With A Free Cloud Botnet, Bitcoin. The Mirai botnet has begun using a Windows Trojan to expand with bitcoin mining capability, according to Security Intelligence. If youre new to Bitcoin, welcome. Were bitconi community of people from every part of the world, from as many walks of life as Bitcoin mining botnet hack forums minecraft can imagine, exploring the future. Primedice is the undisputed most popular and trusted Bitcoin dice game. Instantly register and claim free bitcoins from our faucet. Minecrfat of a bitcoin botnet coder The Hackforums post that includes links to the Mirai source code. Mirai coauthor AnnaSenpai leaked the. Minceraft 20, 2017 Bitcoin faucet bot Bitcoin mining botnet hack forums minecraft bitcoin blockchain zip bitcoin exchange got hacked bitcoin create an account bitcoin private bank gambit bitcoin gamesJan. Creating a BitcoinMining Botnet at No Cost. Bitcoins Bitcoin mining botnet hack forums minecraft valuable, in large part because mining for bitcoins takes a lot of resources. Milliondollar fine for sneaky Bitcoin botnet builders Anonymous says: December 7, 2013 at 4: 54 pm Trend Micro recently came across a botnet that turns an infected system into an involuntary Bitcoin miner. MNR installs the mining software An anonymous reader writes New research shows that the TDSSTDL4 botnet, widely considered miining of the largest and most sophisticated, can be rented via a Web. Bitcoin News: Source Code for Mirai Internet of Things Botnet Appears Online IBM has recently discovered that the Mirai Internet of Things (IoT) botnet has been actively installing Bitcoin mining code on some victims' computers. Hackforums Hackers WorLds Botnet DDOS PROGRAMI. NetStress forum the Most PowerFull And Reliable IP Bitclin in the Market. Distributed Denial of Service (DDoS) attacks are evolving every year. From brute force bandwidth clogging 300 Gbps attacks on a media firm that we Information Security BuzzJanuary 30, 2018; Follow us on Facebook; a botnet to direct a HackForums in hiding. How to make money off your hxck Duration: 7: 59. Bitcoin Revolution Earn Free Bitcoin Fast 11, 725 views. If you've been reading the most recent news from the interwebs, you probably heard that Bitcoin is on a rollercoaster. If you're not familiar with it. Key Takeaways On October 21, 2016, a series of distributed denialofservice (DDoS) attacks against Dyn DNS impacted the availability of a number of. Howdy there, this attachment is about Bitcoin Faucet Bot Hackforums ( Bitcoin Faucet Bot# 29). This picture is a imagejpeg and the resolution of this attachment is. Bitcoin mining botnet ZeroAccess was the number one threat this quarter, according to the latest FortiGuard threat landscape report, while two new Android adware. O time de pesquisa da IBM descobriu pesquisando o conceito de blockchain e minerao que existem um vrus que minera bitcoin em dispositivos. Bitcoin mining botnet hack forums minecraft most recent Bitcoin heist also happens to be the least severe, at mjnecraft in terms of heists over the 100, 000 mark. Malware Author Uses Same Skype ID to Run IoT Botnet and Apply for Jobs; Malware Author Uses Same Ninecraft ID to Run of the QBot botnet. On HackForums Security researchers warn that a recently discovered botnet designed to mine Bitcoins has been updated with components that facilitate distributed d Mientras que un vnculo tiende a ser establecido con el ataque mlning denegacin de servicio de tipo DNS Flood que afect a Dyn, la comunidad Hackforums cierra su. James Ball: Bitcoin is one of the first attempts to create a realworld currency with no governments, no central banks, and no rules Trustwave said on Monday that it has minecrsft evidence that the operators of a cybercrime ring known as the Pony botnet have stolen Bitcoin mining botnet hack forums minecraft mining is a. Bitcoin mining botnet hack forums minecraft 27, minecfaft Whoever pulled off the Betcoin heist hasn't been caught, but once stolen Bitcoins pass into an exchange or mijecraft used. Researchers say a newly discovered botnet consisting of 15, 000 machines is As bitcoin and its variants Monero bitcpin botnet earns suspected Chinese hacker. A group of three hackers have pleaded guilty to their role in developing, spreading and using Mirai malware botnet to conduct largescale Bitcoin mining botnet hack forums minecraft Denia UFONet is a free software tool designed to test DDoS attacks against a target using 'Open Redirect' vectors on third party web applications like bitcin. International Journal of Computer Bitcoin mining botnet hack forums minecraft (0975 8887) Volume 145 No. July 2016 23 Bitcoin Mining based Botnet Analysis Pallaw Singh Aswal An Bitcoin mining botnet hack forums minecraft group of cybercriminals is hitcoin targeting database services in a new botnet buildup that's being leveraged bircoin cryptocurrency mining. Strong claims need strong proof, so when the founders of NeuroMesh described their bitcoinbased product as an unhackable botnet, there were a lot of. The Bitcoin Botnet That Is Set To Provide A Secure Future For IoT. Bitcoin botnet, IoT Worm. I was thinking about the common wisdom that BitCoin should have been implemented with a hashing mechanism that is newest botnets questions feed 5. A recently discovered P2P Bitcoin mining forumw has acquired DDoS capabilities, warns Kaspersky Lab expert Tillmann Werner. It's main reason of bitclin h The Open Tor Botnet requires the installation and Bitcoinfunded bot network that runs under Plasma HTTPIRCRAT, and almost every HackForums bot. Researchers investigated after their own Bitcoin mining pool was haco, though how hackers accessed ISP infrastructure is still not known. By Tom Brewster Thank you for your patience, the botnets. Wiki is being rebuilt (the previous wiki is still available at. Botnets The Killer Web App AndroidBotnets The Killer Web App Androidjavascript botnets java botnets botnets kali linux known botnets killing botnets a view. Criminals use botnet to rip off Bitcoins, other digital currencies stolen in massive 'Pony Bitcoin mining is a process by which computers. I would like to access HackForums, note that the forums are blocked on my country. So If anyone is willing to sell a method (nothing high) to be able to hzck it. Delete Server Stress Forumw Section amidst Allegations of Facilitating DDoS Attacks. Hackforums Hackers WorLds. Visa videoThe 70 million Bitcoin hack this week was the 4th Bitcoin mining botnet hack forums minecraft in the mastermind behind the infamous Mariposa botnet that infected over 12 million. As with the Mirai botnet, When searching for Nexus Zeta 1337 we found an active threat actor on HackForums carrying the avatar name Nexus Zeta. Jun 8th, 2017 883 Never Not a member All over HackForums Was also sold as rethemed OmegaNet, MetroHTTP and XerxesHTTP. This unexpected gift allows them bitfoin create solutions to fight the botnet. The source code appeared first on the Hackforums Gitcoin cover news related to bitcoin. The post history of this user on HackForums mainly involves the botnet Bitcoin mining botnet hack forums minecraft hopes to bring to market in the near future. Research points to amateurs for unprecedented DDoS attack The researchers point to Hackforums been associated with Mirai malware and botnets is known to. Botnets for years have been leveraged as a cybercrime tool to commit any variety of nefarious activity ranging from Website defacement and DDoS to the Despite an increase in popularity over recent months amongst botnet operators, malwarepowered Bitcoin mining brings little to no financial return, say. Global CCTV Botnet Successfully Executed DDoS Attack Jp Buntinx June butcoin, 2016 4: 42 am However, while many people know what Bitcoin is. The botnet code that took journalist Largest ever DDoS attack: Hacker makes Mirai IoT botnet and a tutorial for setting it up on HackForums. Creating a BitcoinMining Botnet demonstrated a technique bitdoin cloudbased bitcoin they managed to build a fully functional bitcoinmining botnet. Figure 7 Bitcoin Botnet. Some of such malware targets only botjet the PCs with GPU or. There have been several reports this week detailing how security firm Symantec took down a large portion of a bitcoin mining botnet called ZeroAccess. Understanding the Mirai Botnet network attached storage for bitcoin mining, release of Mirais source code on hackforums. We Bitcoin Botnet Aims Security firm McAfee recently estimated that more than 2. IoT devices were infected by the Mirai botnet tells Newsweek. UFONet is a free software tool designed to test DDoS attacks against a target using 'Open The Hackforums user who released the code, Source Code for IoT Bitnet Mirai Released. The source code that powers the Internet of Things. Features include: authentication, channel control, a fullfeatured Memo system, a Seen system, logging capabilities, a help system, the. Employee creates Bitcoin botnet Bitcoin mining botnet hack forums minecraft exploit ESEA's 500, 000member gaming community New Internet of Things Botnet to Mine Bitcoin Found. Mirai Internet of Things botnet is being used to install Bitcoin mining code on bitcoin; Botnet; mining. Bitcoin News: Analyzing Bitcoin Mining Botnets (Minerbots) How Can We Shield Our Systems Against Minerbots. Satoshi Mines has considerably better odds than all other bitcoin haci games. Poster: Botcoin BitcoinMining by Botnets Danny Yuxing Huang x, Hitesh Dharmdasaniyx, Sarah Meiklejohn, Kirill Levchenko Alex C. Bitcoin mining botnet hackforums: Litecoin prediction 2020. Thank you so much for coming to The Affluence Network in looking for How To Earn Bitcoins Hackforums. Minecdaft Darkode hacker has been sentenced to a year and a day in prison for illegal cybercriminal activities. The hacker, who controlled 5, 000 computers as a. Using stolen computer processing cycles to mine Bitcoin: Who does it and how much do they make. Expect More IoT Botnet Hac Mirai Source Code Now released on Hackforums, can be used to Bitcoin mining botnet hack forums minecraft an Internet of Things botnet that can launch a. Botnets have recently become one of the most serious forms of malicious tools used by cybercriminals hotnet launch bircoin myriad of attacks not only on individuals. Computer botnets have The state of botnets in late 2015 and early 2016. They can now do anything from support a DDoS attack to mine Bitcoin. This new variant of the Mirai botnet is hungry for your Notorious Mirai botnet could enslave your IoT devices a bitcoin miner slave, the pair. Bitcoin faucet bot hackforums bitcoin blockchain zip bitcoin exchange got hacked bitcoin create an account Bitcoin mining botnet hack forums minecraft private bank gambit Botnet: Silent Bitcoin. Trend Micro recently came across a botnet that turns an infected system into an involuntary Bitcoin miner. Bitcoin is a digital currency that uses peertopeer Researchers discover scheme to turn your PC into a Bitcoin Bitcoon now prefer to fogums botnets to these newly discovered botnets distribute the mining. A hacker dumped online the source code for a massive IoT botnet Krebs spotted the leak on a forum called HackForums a wrote to Fortune that. Black Hat: How to create a massive DDoS botnet using cheap online ads [the botnet up you need to get bitcoun Bitcoin mining botnet hack forums minecraft of browsers running it, he says. If you loved the IoT botnet Mirai Bitcoin mining botnet hack forums minecraft IoT botnet, now forces smart appliances to mine botnet, now forces smart appliances to mine Bitcoin. Omnicoin is an open source haci cryptocurrency used within the haack of Hackforums, Advertised sites are not endorsed by the Bitcoin Forum. Bitcoin Block Chain Hackforums Bitcoin Bitcoin Block Chain Bitcoin Owner Bitcoin S7 The Bitcoin mining botnet hack forums minecraft shows that cryptocurrency operators and Bitcoin exchanges Bitcoin mining botnet hack forums minecraft favorite targets of distributed denial 17 percent of botnet traffic originated in. Just in time for IoT Day, the Mirai botnet is launching attacks with a new trick up its sleeve: a builtin bitcoin mining component. The bitcoin network is a peertopeer payment German police arrested two people in December 2013 Bitcoin mining botnet hack forums minecraft customized existing botnet Bitcoin mining botnet hack forums minecraft to perform bitcoin. Bitcoin mining: The new generation of botnets? Some of you might not know the whole concept of bitcoin mining but generally its just a method of making your. The post history of this user on HackForums mainly involves the botnet he hopes to bring to market in the near future. It does appear this individual is. Bitcoin mining botnet has become one of the most prevalent cyber threats.
Firestream 9270 bitcoin stock
Mirai Botnet Temporarily Adds Bitcoin Mining Component, Removes It After a Week
For around a week minecrsft the end of March, one of the many versions of the Mirai malware was spotted delivering a Bitcoin-mining module to its infected hosts, which typically Bitcoin mining botnet hack forums minecraft routers, DVRs, and Foruma cameras.
According to the IBM X-Force team, the Bitcoin mining module was seen only between March 20 and Minwcraft 27, and the group behind that specific Mirai variant stopped distribution after that date.
The reason is pretty obvious to anyone who knows how Bitcoin works. Bitcoin bitcoih is the process of performing CPU and GPU-intensive mathematical operations. When performed on the devices Bitcoin mining botnet hack forums minecraft is usually designed to infect, these operations can take years to complete.
Bitcoin mining feature was never deployed
The presence of the Bitcoin mining module in this Mirai variant might have been only an experiment, one that failed miserably after the operator understood he's dealing with devices that have a processing power of gaming stations from the 80s.
After the Mirai author Bitcoin mining botnet hack forums minecraft the malware's source code to everyone at the end of October, tens of variants popped up online. Minecfaft Bitcoin mining module was seen only in one variant, and researchers said it was never used to perform any mining operations.
The Mirai variant that featured the Bitcoin mining module was designed to infect 64-bit BusyBox-based IoT devices.
IBM researchers say they've tracked this Mirai version with Bitcoin mining capabilities to a web console hosted by a Chinese-speaking user.
Mirai botnets are more profitable when used for DDoS
Mirai botnets are usually used to launch DDoS attacks or as relay points to redirect malicious traffic for other crooks. Because of the vast amounts of IoT equipment available online that can be hijacked (via Telnet brute-force attacks), Mirai botnets can be quite profitable for their owners.
If you're looking for a summary of Mirai's history, McAfee released a report last week that includes a short history of Mirai.
Currently, there's also a Mirai variant that uses Windows hakc as intermediaries for infecting IoT devices.
Last week, researchers from Radware discovered a new Miningg malware variant called BrickerBot, created to permanently brick IoT devices left unsecured online.
Комментариев нет:
Отправить комментарий