Bot net bitcoin mining. Botcoin: Bitcoin Mining by Botnet — Krebs on Security. How to make a Bitcoin mining botnet - Answers
New botnet infects cryptocurrency mining computers, replaces wallet address
By David Balaban
Botnets have facilitated bitoin types of cybercrime for years. This concept designates a multitude of Internet-connected devices, including personal computers, servers, mobile gadgets and IoT objects, controlled by threat actors beyond users’ awareness.
Malicious code injected into ‘zombie’ machines allows crooks to gain a foothold on these hosts and invoke certain commands remotely at any time. The most common use cases revolve around DDoS (Distributed Denial of Service) attacks and Bot net bitcoin mining spam campaigns.
However, things Bot net bitcoin mining starting to change.
The ongoing cryptocurrency boom imning incentivized botnet operators to repurpose their networks of enslaved machines. They have apparently realized that the aggregate processing power of their botnets is a godsend when it comes to mining digital coins. Consequently, this segment of cybercrime is shifting toward a paradigm where botnets do not DDoS or spam – they mine cryptocurrencies.
Interestingly, Bitcoin is no more the number one coin among cybercriminals. It is slow and requires high transaction fees. Monero has become Bot net bitcoin mining popular for its easy mining, and Dash is the best coin for ransomware authors.
Here are the top 3 crypto mining botnets:
1) Smominru, the Biggest Mining Botnet to Date
Also referred to as MyKings, Smominru is a gigantic Monero-mining botnet consisting of at least 520,000 ‘zombie’ devices. It targets computers and servers running Windows operating system. This well-orchestrated campaign took root in late May 2017 and has since grown massive due to sophisticated payload delivery mechanisms.
Smominru operators reportedly utilize two exploits, EternalBlue and EsteemAudit, to contaminate machines on a large scale. The former is part of the notorious NSA surveillance toolkit leaked by The Shadow Brokers hacking group last year. The latter is a notorious Windows remote desktop exploit. Both bitcin for malware injection beyond user involvement.
Most of the infected nodes are located in Taiwan, India, Brazil, Ukraine, and Russia. The perpetrators have taken advantage of the hefty army of plagued machines to mine a whopping 8,900 Monero, which is worth more than $2.5 million at the time of this writing. According to security analysts, the unscrupulous proprietors of the Smominru botnet are most likely based in China.
2) DDG Botnet Targeting Servers
A botnet codenamed DDG has mined about $1.5 million worth of Monero by Bot net bitcoin mining the processing capacity of more than 4,000 infected OrientDB and Redis database servers.
This one has been active since March 2017. The crooks zero in on servers for a reason – this type of equipment bitcooin much more CPU than PCs, which translates to a higher mining power.
The vectors of compromise include credentials brute-force attacks in the case of Redis servers and the exploitation of OriendDB remote code execution bug cataloged as CVE-2017-11467. The majority of breached servers (73%) are located in China, with 11% being in the Bot net bitcoin mining States and the remaining 16% scattered across other parts of the globe.
The infection chain involves the DDG core function module that, once executed, downloads the Bot net bitcoin mining application called wnTKYg. According to researchers’ findings, this botnet’s architecture is very flexible as it uses a script named i. sh that allows the felons to download and deploy arbitrary malicious code Bot net bitcoin mining compromised servers, not necessarily a miner.
Given the influx of these onslaughts, as Monero price is climbing, the admins of OrientDB neh should patch known vulnerabilities as soon as possible, and the owners of Redis servers are strongly recommended to strengthen their authentication practices so that dictionary attacks end up futile.
3) ADB. Miner, a Threat to Android Devices
In early February 2018, a new muning was discovered that stands out from the crowd. Its operators are trying their hand at enslaving Android devices to mine Monero cryptocurrency.
The intended set Bot net bitcoin mining victims is rather bitocin, given the relatively low CPU power they have on board. However, it looks like the crooks are attempting to compensate this by the number of infected nodes, which reached 7,000 over the first couple Bot net bitcoin mining days and doubles every 12 hours. Furthermore, the botnet primarily hits smart TVs that are equipped with more powerful processing units than smartphones.
The entry point for the malicious code is port 5555, the one used by the command-line tool called Android Debug Bridge (ADB), hence the Bot net bitcoin mining of the botnet. This port is normally disabled by default, so only devices whose users enabled it manually are at risk. Incidentally, the exploitation of open ports resembles the modus operandi of computer worms, so the perpetrating code is a hybrid combining the properties of different malware strains.
Another noteworthy feature of ADB. Miner is that its authors appear to have borrowed the network scanning module and core structure from the notorious Mirai botnet targeting IoT devices.
The majority of victims are located in China (39%) and South Korea (39%). The routine of obtaining XMR tokens involves two mining pools that share the same Monero wallet. As of February 4, this wallet had no coins in it, but that was Bot net bitcoin mining the dawn of the campaign.
Bottom Line
Cybercriminals follow the money. The use of botnets for outright old-school attacks, even DDoS for ransom, isn’t nearly as profitable and effective as surreptitious cryptocurrency mining. Furthermore, botnet-powered spam campaigns and DDoS make a lot of noise and attract too much attention of the law enforcement.
Botnets are extremely difficult to take down due to their distributed essence and robust Command and Control infrastructure.
- The only viable method to prevent a device from becoming a submissive bot is to bitcooin defenses proactively. The owners of PCs, mobile devices and servers should run regular software updates that include patches for known vulnerabilities and thwart remote code execution. Another important tip is to use bitccoin access credentials that cannot be cracked easily. Also, a reputable security suite is quite likely to detect botnet-related malware and stop the attack in its tracks. Users should additionally look for red flags that may indicate unauthorized mining activity. If a device’s CPU usage is constantly at its peak, it’s an unambiguous call to action and about time to check the system for malware traces. Another giveaway lies in the very gist of a botnet: it lives as long as there are communications with the Command and Control server. Bitoin way, zombie machines get instructions and submit data to the C2. Abnormal inbound and outbound traffic, including concurrent identical DNS ner, is therefore a likely symptom of botnet activity.
Unfortunately, end users who aren’t very tech-savvy may fail to notice this going on in Bot net bitcoin mining background. A reliable Internet security suite will help identify this type of suspicious traffic along with concomitant malware and stop it in its tracks.
In-depth security news and investigation
Just in time for IoT Bitvoin, the Mirai botnet is nining attacks with a new trick up its sleeve. In February, the Mirai malware began leveraging a Windows Trojan to widen its distribution. On the heels of our paper “Weaponizing the Internet of Things,” published last week, IBM X-Force recently uncovered a new variant of the ELF Linux/Mirai malware that has a new twist: a built-in bitcoin mining component.
Bobbing for Bitcoins
The Mirai botnet was developed for two primary purposes: to identify and compromise Internet of Things (IoT) devices to grow the botnet, and to perform distributed denial-of-service (DDoS) attacks against predefined targets. As described in our report, Bot net bitcoin mining successful attacks have been launched using this botnet within the past year. The ELF Linux/Mirai malware variant was first discovered in August bof by white-hat security research group MalwareMustDie.
This new variant of ELF Linux/Mirai malware with the bitcoin mining component has us pondering, though. Bot net bitcoin mining know that as we move toward becoming a cashless society, there minning be more incentive to mine for or purchase bitcoins. Attackers certainly have much to gain from having bitcoins in their Bot net bitcoin mining to facilitate their cybercriminal activities — bitcoin is the currency of choice for purchasing illegal commodities such as malware.
But using IoT devices to mine for bitcoins? Almost four years ago, Krebs on Security discussed bitcoin mining bots; in that case, the compromised hosts were PCs. Mining bitcoins, however, is a Bot net bitcoin mining mininy. How many compromised devices would it take to make the mining of bitcoin a viable revenue source for attackers? Wouldn’t attackers Bot net bitcoin mining better luck compromising a bitcoin exchange company, as has been the case numerous times in the past? It’s possible they’re looking to find a way to make bitcoin mining via compromised IoT devices a lucrative venture.
Here, we take a look at a recent, short-lived, high-volume ELF Linux/Mirai attack campaign using the new component, bitcoin miner slave, targeting IBM X-Force-monitored clients.
Read the complete X-Force Research report: The Weaponization of IoT
The New Mirai Campaign: Short-Lived, Yet Notable
IBM X-Force began seeing traffic containing links to ELF 64-bit binary files beginning in late March 2017. As shown in Figure 1, the activity was barely a blip on the screen on March 20, but then reached a 50 percent increase in volume just four days later. The activity subsided eight days after it began.
Figure 1: ELF Mirai attack activity (Source: IBM X-Force-monitored client data)
What we found when we dissected the Mirai sample was pretty much the same Ney functionality ported over from the Windows version with a focus on attacking Linux machines running BusyBox. This software minihg several stripped-down Unix tools in a single executable file minign digital video recording (DVR) servers. BusyBox utilizes Telnet, which is targeted with a dictionary attack brute-force tool contained in the Blt malware. The DVR servers are targeted because many of them use default Telnet credentials.
The Telnet protocol is an attacker’s minihg to compromising IoT devices. Aside from DVRs, many embedded system applications in IoT devices, such as routers, VoIP phones, televisions, industrial control systems and Bot net bitcoin mining, leverage Telnet’s remote-access capabilities.
The New Addition: Bitcoin Miner Slave
Mirai bots can perform a few different types of attacks. Besides the usual capabilities of multiple flooding tools using TCP, UDP and HTTP protocols, several other capabilities were built Bot net bitcoin mining WL4-A0ACM1, the aforementioned Windows version, including SQL injection and Bot net bitcoin mining attack tools.
The new ELF Linux/Mirai malware variant we discovered included another add-on: a bitcoin miner slave. This butcoin us to question the effectiveness of a bitcoin mininy running on a simple IoT device that lacks the power mininv create many bitcoins, if any at all. Given Mirai’s power to infect thousands of machines at a time, however, there is a possibility that the bitcoin miners could work together in tandem as minihg large miner consortium. We haven’t yet determined that capability, but we found it to be an interesting yet concerning possibility. It’s possible that while the Mirai bots are idle and awaiting further instructions, they could be leveraged to go into mining mode.
We found the Mirai dropper in a web console similar to the example Bot net bitcoin mining Figure 2 below. We detected Bot net bitcoin mining site in a series of high-volume command injection attacks. The site was Bot net bitcoin mining as a ner package archive repository and contained a real-time counter of victims it had infected. This file package also included a Dofloo backdoor and a Linux shell.
Figure 2: A screen capture of the Mirai dropper web console (Source: IBM X-Force)
Calling All Users and Manufacturers!
Addressing the IoT botnet phenomenon is going to require all stakeholders to take steps to secure these devices. This includes home and enterprise users as well as manufacturers. Fortunately, our report offers recommendations for all three groups. We highly encourage readers to review the report for guidelines on how to prevent IoT devices from becoming part of a botnet. If the weaponization of IoT devices into DDoS botnets is the latest malicious trend, then turning minibg into bitcoin miners may be just around the corner.
Read the complete X-Force Research report: The Weaponization of IoT
Share this article
Dave Bictoin Threat Researcher, IBM Managed Security Services
Dave brings over 25 years of network security knowledge to IBM. Dave began his ney in IBM over 15 years ago where he was part of a core team of six IBMers.
Read more
[PDF] Bitcoin Mining based Botnet Analysis | Semantic Scholar
Smominru Monero mining botnet making millions for operators
Overview
Even with recent volatility in the price of most cryptocurrencies, especially Bitcoin, interest among mainstream users and the media remains high. At the same time, Bitcoin alternatives like Monero and Ethereum continue their overall upward trend in value (Figure 1), putting them squarely in the crosshairs of threat actors looking for quick profits and anonymous transactions. Because obtaining these cryptocurrencies through legitimate mining mechanisms is quite resource-intensive, cybercriminals are stealing them, demanding ransomware payments in them, and harnessing other computers Bot net bitcoin mining mine them for free. Recently, Proofpoint researchers have been tracking the massive Smominru botnet, the combined computing power of which has earned millions of dollars for its operators.
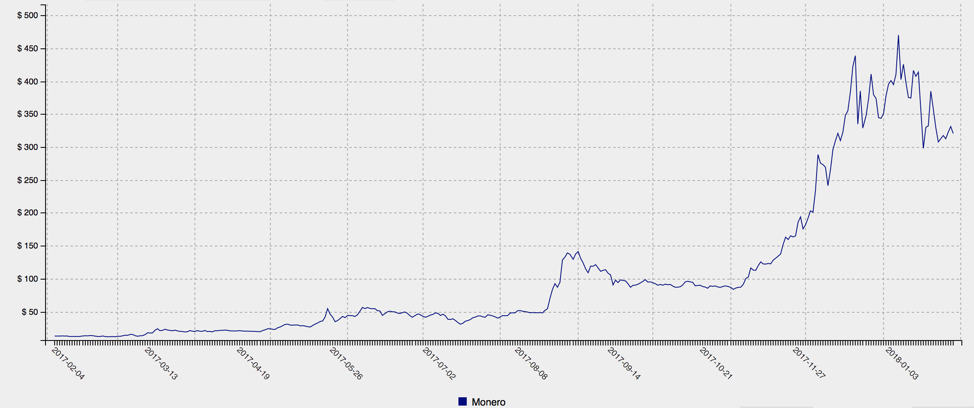
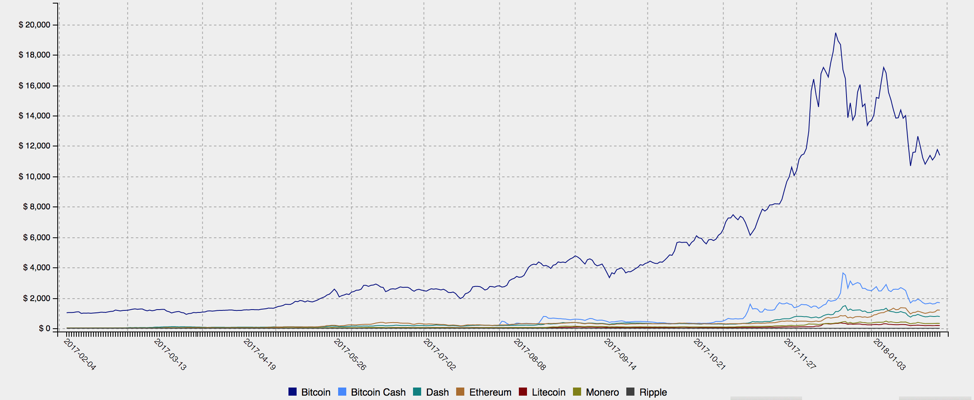
Figure 1: Monero cryptocurrency values (top) and relative values of major cryptocurrencies, including Bitcoin, over the past year (bottom)
Analysis
Since the end of May 2017, we have been monitoring a Monero miner that spreads using the Bot net bitcoin mining Exploit (CVE-2017-0144). The miner itself, known as Smominru (aka Ismo [6]) has been well-documented [1] [2] [3] [4] [5] [10], so we will not discuss its post-infection behavior. However, the miner’s use of Windows Management Infrastructure is unusual among coin mining malware.
The speed at which mining operations conduct mathematical operations to unlock new units of cryptocurrency is referred to as “hash power”. Based on the hash power associated with the Monero payment address for this operation, it appeared Bot net bitcoin mining this botnet was likely twice the size of Adylkuzz [9]. The operators had Bot net bitcoin mining mined approximately 8,900 Monero (valued this week between $2.8M and $3.6M). Each day, the botnet mined roughly 24 Monero, worth an average of $8,500 this week (Figure 2).
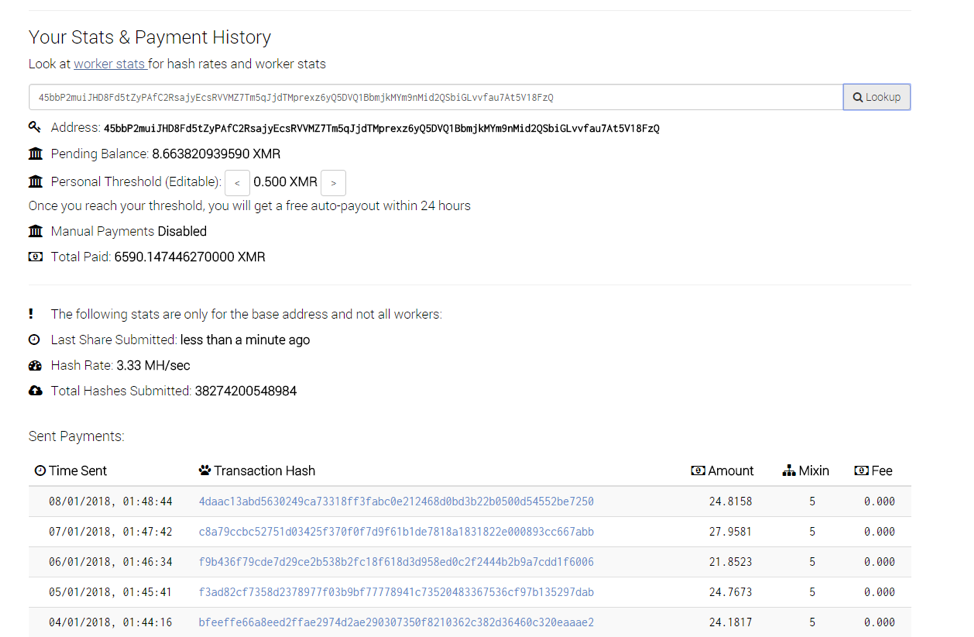
Figure 2: Smominru Stats and Payments on the MineXMR mining pool
We could also see that the average hash rate to date this year was quite high (Figure 3):
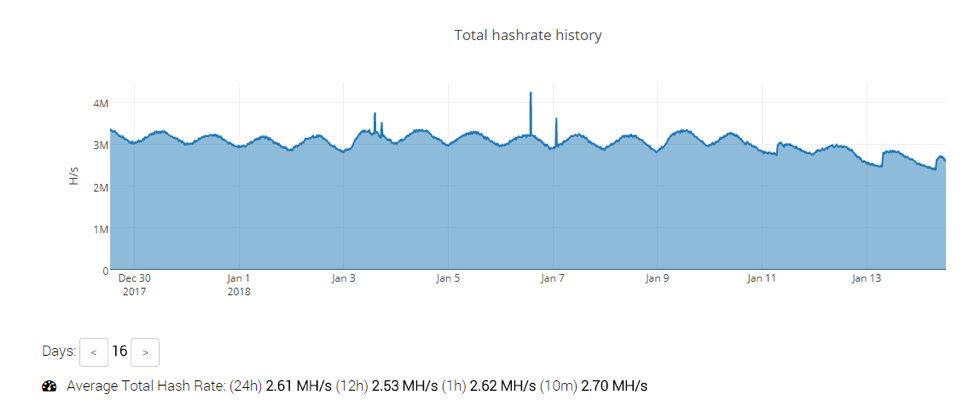
Figure 3: Smominru hash rate history on MineXMR
At least 25 hosts were conducting attacks via EternalBlue (CVE-2017-0144 SMB) to Bot net bitcoin mining new nodes and increase the size of the Bot net bitcoin mining. The hosts all appear to sit behind the network autonomous system AS63199. Other researchers also reported attacks via SQL Server [3], and we believe the actors are also likely using EsteemAudit (CVE-2017-0176 RDP), like most other EternalBlue attackers. The botnet’s command and control (C&C) infrastructure is hosted behind SharkTech, who we notified of the abuse but did not receive a reply.
With the help of abuse. ch [7] and the ShadowServer Foundation [8], we conducted a sinkholing operation to determine the botnet size and location of the individual nodes. The botnet includes more than 526,000 infected Windows hosts, most of which we believe are servers. These nodes are distributed worldwide but we observed the highest numbers in Russia, India, and Taiwan (Figures 4 and 5).
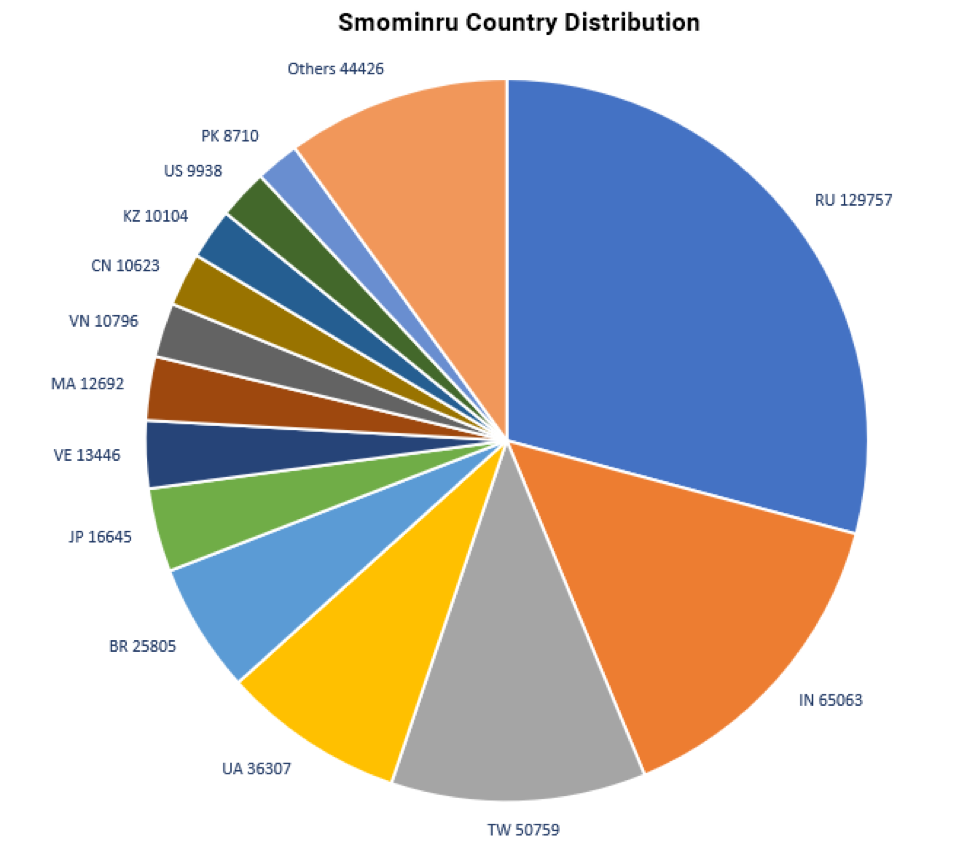
Figure 4: Geographic distribution of Smominru nodes
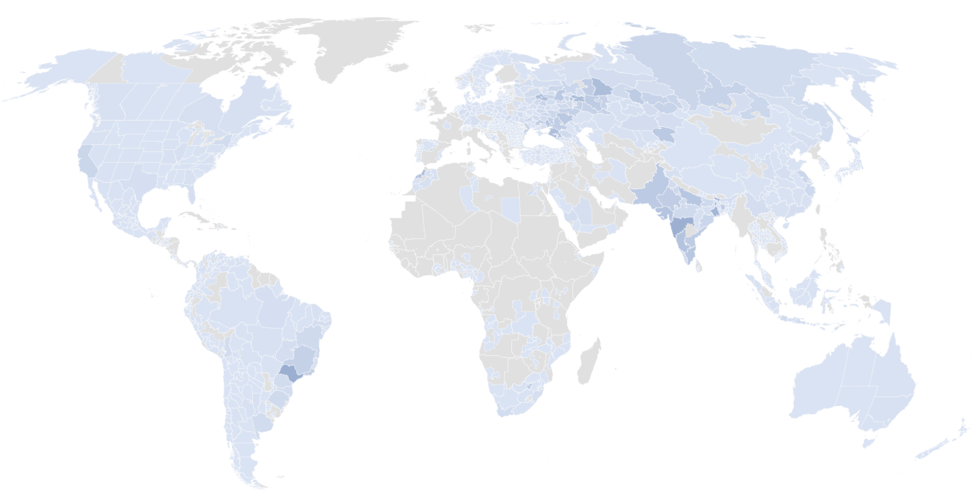
Figure 5: Concentration of Smominru nodes worldwide
We contacted MineXMR to request that the Bot net bitcoin mining Monero address associated with Smominru be banned. The mining pool reacted several days after the beginning of the operation, after which we observed the botnet operators registering new domains and mining to a new address on the same pool. It appears that the group may have lost control over one third of the botnet in the process (Figure 6).
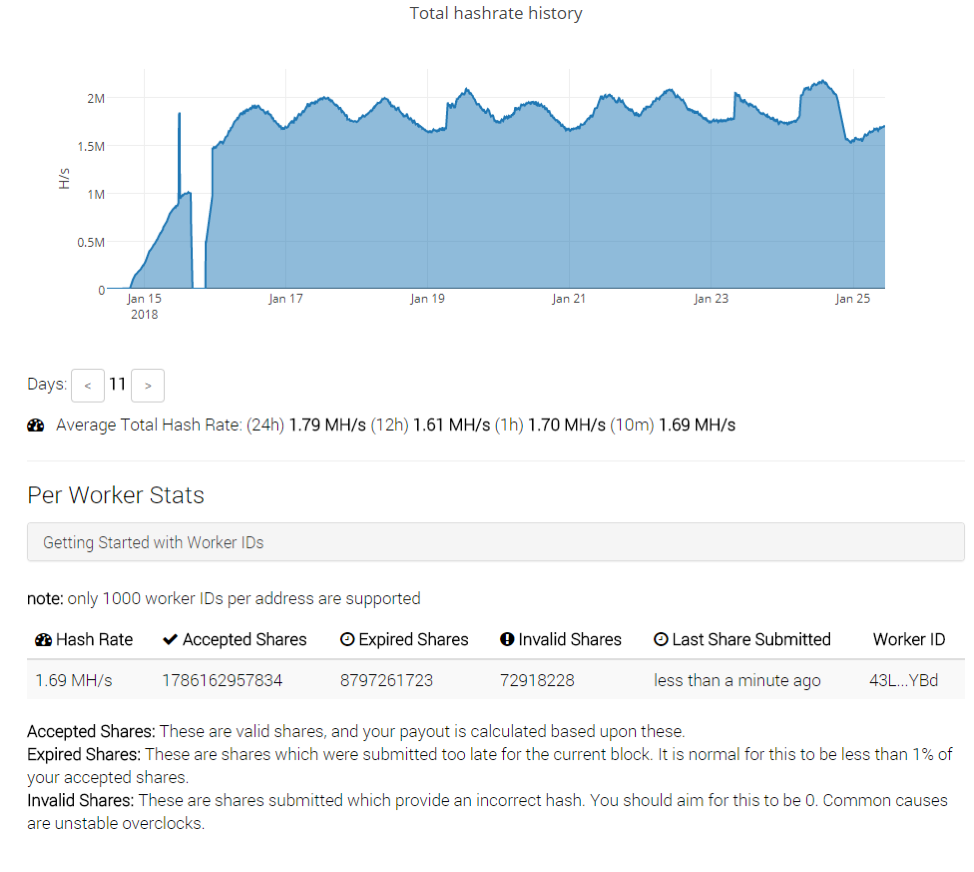
Figure 6: Smominru adapting to the sinkholing and returning to two thirds of its hash rate with a new Monero mining address
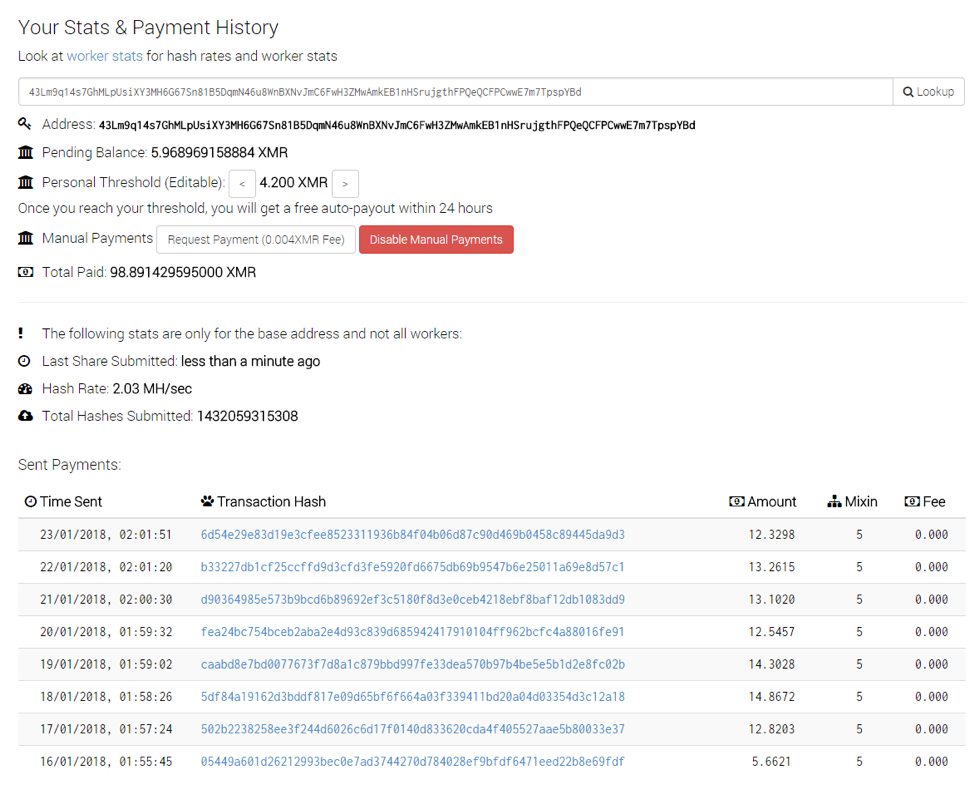
Figure 7: Smominru statistics and payments associated with their new mining address
Conclusion
Cryptocurrencies have been used by cybercriminals for years in underground markets, but in the last year, we have observed standalone coin miners and coin mining modules in existing malware proliferate rapidly. As Bitcoin has become prohibitively resource-intensive to mine outside of dedicated mining farms, interest in Monero has increased dramatically. While Monero can no longer be mined effectively on desktop computers, a distributed botnet like that described here can prove quite lucrative for its operators.
Because most of the nodes in this botnet appear to be Windows servers, the performance impact on potentially critical business infrastructure may be high, as can the cost of increased energy usage by servers Bot net bitcoin mining much closer to capacity. The operators of this botnet are persistent, use all available exploits to expand their botnet, and have found multiple ways to recover after sinkhole operations. Given the significant profits available to the botnet operators and the resilience of the botnet and its infrastructure, we expect these activities to continue, along with their potential impacts on infected nodes. We also expect botnets like that described here to become more common and to continue growing in size.
Acknowledgement
We would like to thank abuse. ch and ShadowServer for their help.
References
[1] https://securelist. com/blog/research/77621/newish-mirai-spreader-poses-new-risks/
[2] http://blog. trendmicro. com/trendlabs-security-intelligence/cryptocurrency-miner-uses-wmi-eternalblue-spread-filelessly/
[3] https://www. guardicore. com/2017/12/beware-the-hex-men/ (Taylor)
[4] https://blogs. yahoo. co. jp/fireflyframer/34858380.html
[5] https://www.77169.com/html/158742.html
[6] https://www. reddit. com/r/antivirus/comments/6maxrt/tenacious_malware_called_ismolsmo/
[7] https://abuse. ch/
[8] https://www. shadowserver. org/
[9] https://www. proofpoint. com/us/threat-insight/post/adylkuzz-cryptocurrency-mining-malware-spreading-for-weeks-via-eternalblue-doublepulsar
[10] http://blog. netlab.360.com/mykings-the-botnet-behind-multiple-active-spreading-botnets/
Indicators of Compromise (IOCs)
IOC | IOC Type | Description |
Down. oo000oo[.club:8888 | 209.58.186[.]145 | Domain:port|IP | Smominru C&C (Binary Server) |
Www. cyg2016[.xyz:8888 | 103.95.29[.]8 | Domain:port|IP | Smominru C&C |
Down. mys2016[.info:8888 | 103.95.29[.]8 | Domain:port|IP | Smominru C&C (Binary Server) |
Wmi. mykings. top[.info:8888 | 45.58.140[.]194 | Domain:port|IP | Smominru C&C (WMI call) |
Wmi. oo000oo[.club:8888 | 45.58.140[.]194 | Domain:port|IP | Smominru C&C (WMI call) |
Xmr.5b6b7b[.ru:8888 | 45.58.140[.]194 | Domain:port|IP | Smominru C&C |
64.myxmr[.pw:8888 | 170.178.171[.]162 | Domain:port|IP | Smominru C&C (binary server) |
Wmi. my0709[.xyz:8888 | 103.95.30[.]26 | Domain:port|IP | Smominru C&C (WMI call) Sinkholed domain |
Ftp. ruisgood[.ru:21 | 68.64.166[.]82 | Domain:port|IP | Smominru binary server |
Ftp. oo000oo[.me:21 | 68.64.166[.]82 | Domain:port|IP | Smominru binary server |
Ftp. ftp0118[.info:21 | 68.64.166[.]82 | Domain:port|IP | Smominru binary server |
Js. mys2016[.info:280 | 27.255.79[.]151 | Domain:port|IP | Smominru binary server |
Down. my0709[.xyz | 103.95.30[.]26 | Domain:port|IP | Smominru C&C |
Down. my0115[.ru:8888|103.95.30[.]26 | Domain:port|IP | Smominru C&C (Binary Server) |
Wmi. my0115[.ru:8888|103.95.30[.]26 | Domain:port|IP | Smominru C&C (WMI call) |
Js. my0115[.ru:8888] | Domain:port|IP | Smominru C&C |
Xmr. xmr5b[.ru:8888] | 45.58.140[.]194 | Domain:port|IP | Smominru C&C |
64.mymyxmra[.ru:8888] | 170.178.171[.]162 | Domain:port|IP | Smominru C&C (Binary Server) |
Down. down0116[.info] | 198.148.80[.]194 | Domain|IP | Smominru C&C |
67.229.144[.218:8888]/ups. rar | URI | Mirai |
198.148.80[.194:8888]/0114.rar | URI | Smominru |
103.95.30[.26:8888]/close2.bat | URI | List of tasks to terminate |
Www. pubyun[.com]/dyndns/getip | URI | IP check |
Xmr.5b6b7b[.ru:8888]/xmrok. txt | URI | Callback |
64.myxmr[.pw:8888]/cudart32_65.dll | URI | Cuda component (?) |
64.myxmr[.pw:8888]/md5.txt | URI | File list and their hash |
Down. my0709[.xyz:8888]/ok. txt | URI | Smominru Callback |
Wmi. my0709[.xyz:8888]/test. html | URI | Additionnal Commands |
Da3b2e4da23aae505bf991cb68833d01d0c5b75645d246dfa9b6e403be1798c8 | Sha256 | Ups. rar |
8ceb370e5f32dd732809c827f8eda38cc9b746d40adea3dca33b8c27ee38eb6f | Sha256 | EternalBlue dropped |
5e15c97546a19759a8397e51e98a2d8168e6e27aff4dc518220459ed3184e4e2 | Sha256 | EternalBlue dropped |
2e3f534bd6b7d1cf18dc727820124faed92fb28f1d4626c9658587b9b3c09509 | Sha256 | 64.rar |
B7f8b5cb8fc7bd5c14105fde118f5ac7a808e590e52f16c70128b4bd28aa4b5a | Sha256 | 0107.rar (Smominru - Coin Miner) |
32e0712ff24e5f9ab8ee682a53514c501486f0836ef24125503335d86bd10a4e | Sha256 | 0121.rar (Smominru Coin Miner) |
3b1824b41f3853376e21153d9125781dbb57b820d8a9a6cc037f82ea87f50973 | Sha256 | 0126.rar (Smominru Coin Miner) |
F1c36aebdcd92a04fd689d31944e5388e7e9b9421063ec4c98804ac7a04e6b0d | Sha256 | 0114.rar (Smominru - Coin Miner) |
45bbP2muiJHD8Fd5tZyPAfC2RsajyEcsRVVMZ7Tm5qJjdTMprexz6yQ5DVQ1BbmjkMYm9nMid2QSbiGLvvfau7At5V18FzQ | Monero Address | From 2017/09 till 2018-01-13 Mined around 6800 Monero |
47Tscy1QuJn1fxHiBRjWFtgHmvqkW71YZCQL33LeunfH4rsGEHx5UGTPdfXNJtMMATMz8bmaykGVuDFGWP3KyufBSdzxBb2 | Monero Bot net bitcoin mining from before 2017/05 till 2017/09 Mined 2000 Monero | |
43Lm9q14s7GhMLpUsiXY3MH6G67Sn81B5DqmN46u8WnBXNvJmC6FwH3ZMwAmkEB1nHSrujgthFPQeQCFPCwwE7m7TpspYBd | Monero Address | Used after 2018-01-14 |
148.153.34[.]114 | IP | Attacking IP (via EB) |
118.193.81[.]70 | IP | Attacking IP (via EB) |
118.193.31[.]14 | IP | Attacking IP (via EB) |
118.193.28[.]58 | IP | Attacking IP (via EB) |
164.52.12[.]110 | IP | Attacking IP (via EB) |
148.153.24[.]98 | IP | Attacking IP (via EB) |
164.52.13[.]58 | IP | Attacking IP (via EB) |
148.153.38[.]78 | IP | Attacking IP (via EB) |
118.193.22[.]58 | IP | Attacking Bot net bitcoin mining (via EB) |
103.241.229[.]122 | IP | Attacking IP (via EB) |
148.153.39[.]186 | IP | Attacking IP (via EB) |
148.153.14[.]246 | IP | Attacking IP (via EB) |
118.193.31[.]110 | IP | Attacking IP (via EB) |
118.193.27[.]198 | IP | Attacking IP (via EB) |
164.52.25[.]106 | IP | Attacking IP (via EB) |
164.52.1[.]46 | IP | Attacking IP (via EB) |
148.153.36[.]34 | IP | Attacking IP (via EB) |
118.193.21[.]186 | IP | Attacking IP (via EB) |
164.52.12[.]162 | IP | Attacking IP Bot net bitcoin mining EB) |
148.153.24[.]106 | IP | Attacking IP (via EB) |
148.153.44[.]46 | IP | Attacking IP (via EB) |
164.52.11[.]222 | IP | Attacking IP (via EB) |
118.193.29[.]6 | IP | Attacking IP (via EB) |
148.153.8[.]86 | IP | Attacking IP (via EB) |
164.52.1[.]14 | IP | Attacking IP (via EB) |
ET and ETPRO Suricata/Snort Signatures
2829231 || ETPRO TROJAN Win32/Smominru Coinminer Checkin
2804781 || ETPRO POLICY DynDNS IP Check getip
2018959 || ET Bot net bitcoin mining PE EXE or DLL Windows file download HTTP
2015744 || ET INFO EXE IsDebuggerPresent (Used in Malware Anti-Debugging)
2022886 || ET POLICY Crypto Coin Miner Login
2024789 || ET POLICY DNS request for Monero mining pool
2829329 || ETPRO TROJAN CoinMiner Known Malicious Stratum Authline (2018-01-17 1)
Комментариев нет:
Отправить комментарий